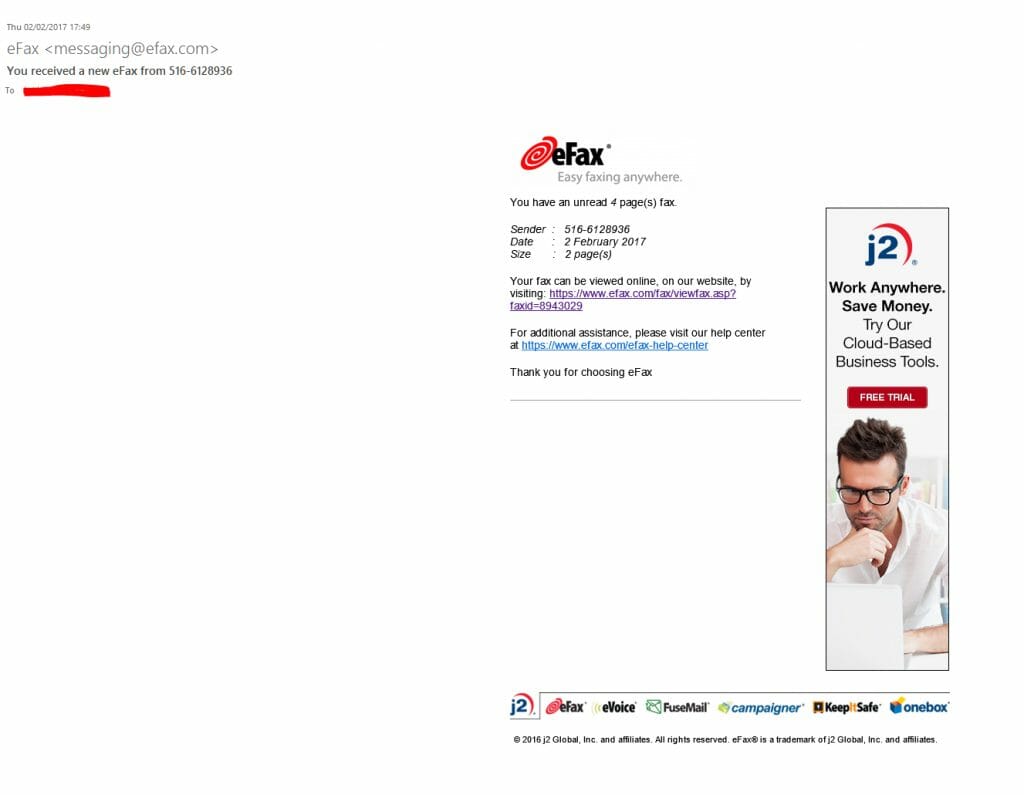
A return of a perennial template with an email with the subject of You received a new eFax from 516-6128936 ( numbers are normally random) pretending to come from eFax <[email protected]> with a link that downloads a malicious word doc. I cannot get any actual payload from the word doc, so I don’t know what malware it is delivering
They are using email addresses and subjects that will scare or entice a user to read the email and open the attachment. A very high proportion are being targeted at small and medium size businesses, with the hope of getting a better response than they do from consumers.
eFax,com has not been hacked or had their email or other servers compromised. They are not sending the emails to you. They are just innocent victims in exactly the same way as every recipient of these emails.
The download link in the body of the email is where the base64 encoded section is the recipients email address. I changed that to read [email protected]. The downloaded word doc is created by adding the recipients name, or at least the bit before the @ in the email address. The word doc contains macros but I cannot get any actual payload. In fact I have never seen macros like these before. They make very interesting reading
Update: I am reliably informed it downloads Hancitor & other associated malware
2 February 2017 : eFax_victim.doc Current Virus total detections: Payload Security
Update 3 February 2017: Today’s version has a .lnk file inside a zip as an attachment ( VirusTotal) connects to & downloads analytics.activeadvisory.com/007.bin but only from a Canadian IP range. The rest of the world appears blocked. ( VirusTotal) ( Payload Security ) This one is delivering Urnsif banking Trojan
The email looks like:
From: eFax <[email protected]>
Date: Thu 02/02/2017 17:49
Subject: You received a new eFax from 516-6128936
Attachment: link in email body
Body content:
You have an unread 4 page(s) fax.
Sender : 516-6128936 Date : 2 February 2017 Size : 2 page(s)
Your fax can be viewed online, on our website, by visiting: https://www.efax.com/fax/viewfax.asp?faxid=8943029
For additional assistance, please visit our help center at https://www.efax.com/efax-help-center
Thank you for choosing eFax
© 2016 j2 Global, Inc. and affiliates. All rights reserved. eFax® is a trademark of j2 Global, Inc. and affiliates.
Screenshot:
Previous campaigns over the last few weeks have delivered numerous different download sites and malware versions. There are frequently 5 or 6 and even up to 150 download locations on some days, sometimes delivering the exactly same malware from all locations and sometimes slightly different malware versions. Dridex /Locky does update at frequent intervals during the day, sometimes as quickly as every hour, so you might get a different version of these nasty Ransomware or Banking password stealer Trojans.
All the alleged senders, companies, names of employees, phone numbers, amounts, reference numbers etc. mentioned in the emails are all innocent and are just picked at random. Some of these companies will exist and some won’t. Don’t try to respond by phone or email, all you will do is end up with an innocent person or company who have had their details spoofed and picked at random from a long list that the bad guys have previously found . The bad guys choose companies, Government departments and other organisations with subjects that are designed to entice you or alarm you into blindly opening the attachment or clicking the link in the email to see what is happening.
This email attachment contains what appears to be a genuine word doc or Excel XLS spreadsheet with either a macro script or an embedded OLE object that when run will infect you.
Modern versions of Microsoft office, that is Office 2010, 2013, 2016 and Office 365 should be automatically set to higher security to protect you.
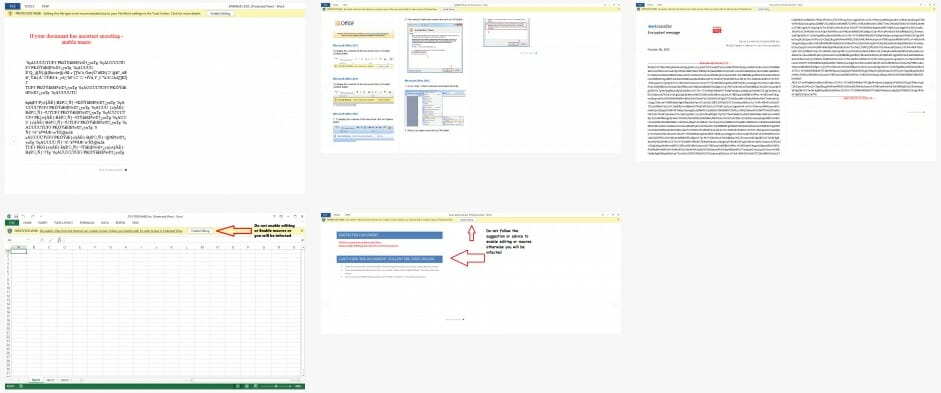
By default protected view is enabled and macros are disabled, UNLESS you or your company have enabled them. If protected view mode is turned off and macros are enabled then opening this malicious word document will infect you, and simply previewing it in windows explorer or your email client might well be enough to infect you. Definitely DO NOT follow the advice they give to enable macros or enable editing to see the content.
Most of these malicious word documents either appear to be totally blank or look something like these images when opened in protected view mode, which should be the default in Office 2010, 2013, 2016 and 365. Some versions pretend to have a digital RSA key and say you need to enable editing and Macros to see the content. Do NOT enable Macros or editing under any circumstances.
What Can Be Infected By This
At this time, these malicious macros only infect windows computers. They do not affect a Mac, IPhone, IPad, Blackberry, Windows phone or Android phone. The malicious word or excel file can open on any device with an office program installed, and potentially the macro will run on Windows or Mac or any other device with Microsoft Office installed.
BUT the downloaded malware that the macro tries to download is windows specific, so will not harm, install or infect any other computer except a windows computer. You will not be infected if you do not have macros enabled in Excel or Word. These Macros do not run in “Office Online” Open Office, Libre Office, Word Perfect or any other office program that can read Word or Excel files.
Please read our How to protect yourselves page for simple, sensible advice on how to avoid being infected by this sort of socially engineered malware. Also please read our post about word macro malware and how to avoid being infected by them
Be very careful with email attachments. All of these emails use Social engineering tricks to persuade you to open the attachments that come with the email. It might be a simple message saying “look at this picture of me I took last night” that appears to come from a friend.
It might be a scare ware message that will make you open the attachment to see what you are accused of doing. Frequently it is more targeted at somebody ( small companies etc.) who regularly receive PDF attachments or Word .doc attachments or any other common file that you use every day, for example an invoice addressed to [email protected].
The basic rule is NEVER open any attachment to an email, unless you are expecting it. Now that is very easy to say but quite hard to put into practice, because we all get emails with files attached to them. Our friends and family love to send us pictures of them doing silly things, or even cute pictures of the children or pets. Many of us routinely get Word, Excel or PowerPoint attachments in the course of work or from companies that we already have a relationship with.
Never just blindly click on the file in your email program. Always save the file to your downloads folder, so you can check it first. A lot of malicious files that are attached to emails will have a faked extension. That is the 3 letters at the end of the file name. Unfortunately windows by default hides the file extensions so you need to Set your folder options to “show known file types.
Then when you unzip the zip file that is supposed to contain the pictures of “Sally’s dog catching a ball”, an invoice or receipt from some company for a product or service or receive a Word doc or Excel file report that work has supposedly sent you to finish working on at the weekend, you can easily see if it is a picture or document & not a malicious program. If you see JS or .EXE or .COM or .PIF or .SCR or .HTA .vbs, .wsf , .jse .jar at the end of the file name DO NOT click on it or try to open it, it will infect you.
With these malformed infected word, excel and other office documents that normally contain a vba macro virus, the vital thing is do not open any office document direct from your email client or the web. Always save the document to a safe location on your computer, normally your downloads folder or your documents folder and scan it with your antivirus. Many Antiviruses do not natively detect vba macro-viruses in real time protection and you need to enable document or office protection in the settings. Do not rely on your Anti-Virus to immediately detect the malware or malicious content. DO NOT enable editing mode or enable macros
All modern versions of word and other office programs, that is 2010, 2013, 2016 and 365, should open all Microsoft office documents that is word docs, excel files and PowerPoint etc that are downloaded from the web or received in an email automatically in “protected view” that stops any embedded malware or macros from being displayed and running.
Make sure protected view is set in all office programs to protect you and your company from these sorts of attacks and do not over ride it to edit the document until you are 100% sure that it is a safe document. If the protected mode bar appears when opening the document DO NOT enable editing mode or enable macros the document will look blank or have a warning message, but will be safe.
Be aware that there are a lot of dodgy word docs spreading that WILL infect you with no action from you if you are still using an out dated or vulnerable version of word. This is a good reason to update your office programs to a recent version and stop using office 2003 and 2007.
Many of us have continued to use older versions of word and other office programs, because they are convenient, have the functions and settings we are used to and have never seen a need to update to the latest super-duper version. The risks in using older version are now seriously starting to outweigh the convenience, benefits and cost of keeping an old version going.
I strongly urge you to update your office software to the latest version and stop putting yourself at risk, using old out of date software.