We are seeing loads of emails with Malformed or infected word docs with embedded macro viruses they are what appears to be a genuine word doc attached which is malformed and contains a macro or vba script virus. Modern versions of Microsoft office, that is Office 2010 and 2013 and Office 365 have Macros disabled by default, UNLESS you or your company have enabled them.
Opening this malicious word document will infect you if Macros are enabled and simply previewing it in windows explorer or your email client might well be enough to infect you. Definitely DO NOT follow the advice the bad guys give to enable macros to see the content.
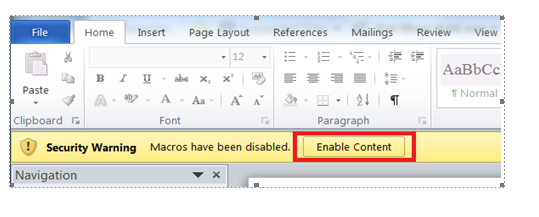
On preview of the attachment, you get this or similar wording and image shown
This error usually occurs because of macro security settings. To check your macro security settings, click the Microsoft Office Button, click Microsoft Word Options, click Trust Center, and then click Trust Center Settings. If macro security is set to Disable all macros without notification, all macros are automatically disabled. Use the following procedure to enable the macro.
In the Trust Center dialog box, click Macro Settings, and then click Disable all macros with notification. Click OK in the Trust Center dialog box to apply the new setting. Click OK to close the program options dialog box. Close the file and the Microsoft Word. Open the file again. A Security Alert appears in the Document Information Bar just below the ribbon. Click Enable Content to allow the macro to run.
 Do not open word docs received in an email without scanning them with your antivirus first and be aware that there are a lot of dodgy word docs spreading that WILL infect you with no action from you if you are still using an out dated or vulnerable version of word. This is a good reason to update your office programs to a recent version and stop using office 2003 and 2007. The risks in using older version are starting to outweigh the convenience, benefits and cost of keeping an old version going.
Do not open word docs received in an email without scanning them with your antivirus first and be aware that there are a lot of dodgy word docs spreading that WILL infect you with no action from you if you are still using an out dated or vulnerable version of word. This is a good reason to update your office programs to a recent version and stop using office 2003 and 2007. The risks in using older version are starting to outweigh the convenience, benefits and cost of keeping an old version going.
I strongly urge you to update your office software to the latest version and stop putting yourself at risk, using old out of date software
All modern versions of word and other office programs, that is 2010, 2013 and 365, should open word docs, excel files and PowerPoint etc that are downloaded from the web or received in an email automatically in “protected view” that stops any embedded malware or macros from being displayed and running. Make sure protected view is set in all office programs to protect you and your company from these sorts of attacks
You must learn and educate others to look at the attachment and if the protected mode bar appears when opening or previewing the document DO NOT enable editing mode the document might look blank, but will be safe. One of the almost certain ways of identifying a malicious document that you have received in an email is that it will not preview in the preview pane in outlook or when saved to your downloads folder and appears blank.
