We see lots of phishing attempts for email credentials. This one is slightly different than many others and much more involved and complicated.
When I received the email I was convinced it was going to be a malware delivery attempt, but instead it is a slightly devious & complicated method of phishing for email credentials.
They use email addresses and subjects that will entice a user to read the email and open the attachment. A very high proportion are being targeted at small and medium size businesses, with the hope of getting a better response than they do from consumers.
You can now submit suspicious sites, emails and files via our Submissions system
Remember many email clients, especially on a mobile phone or tablet, only show the Name in the From: and not the bit in <domain.com >. That is why these scams and phishes work so well.
These do actually come via distell.co.za, or at least via their authorised mail sending service ( mimecast) so it is likely that a user’s log in details have been compromised
The email looks like:
From: Moolman, Enrico <[email protected]>
Date: Tue 29/05/2018 08:00
Subject: Send invoice for payment
Attachment: New_Order.ZIP
Body content:
Hello,
Truth you are doing well,
Please find attached our purchase order for your attention. process and send us proforma so we make payment today, also advice on when we should expect delivery.
Disclaimer
Attention: The legal status of this communication is governed by the terms and conditions published at the following link. For reporting any unethical or fraudulent behaviour, please contact our toll-free anonymous hotline on 0800 004 822.
Visit South Africa’s premier producer and marketer of fine wines, spirits, ciders and ready-to-drinks (RTDs) at http://www.distell.co.za.
Screenshot:
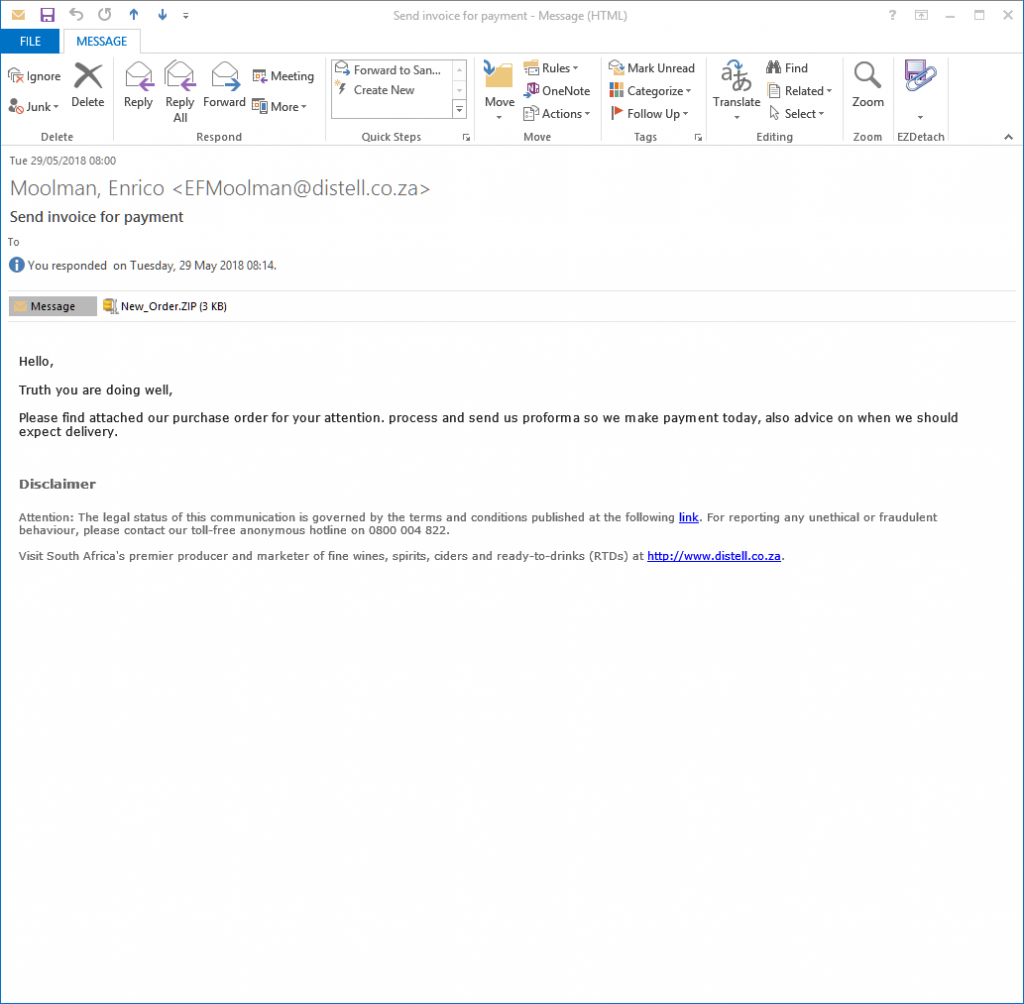
This email has a html attachment in encoded url format that when opened in browser shows you a webpage like this with a small image of an order or invoice and a link to view document.
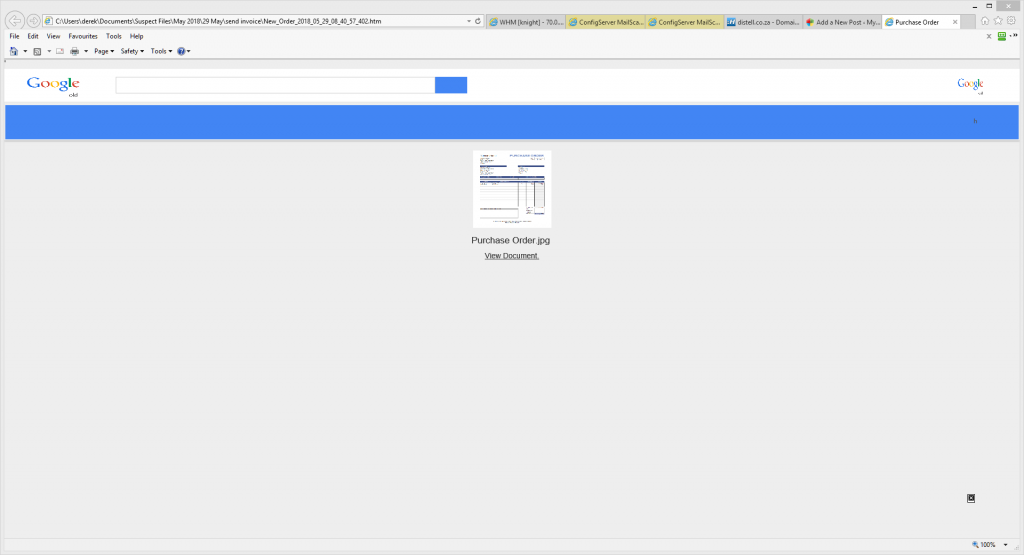
Once you click the view Document link you see this page, where you can input your details
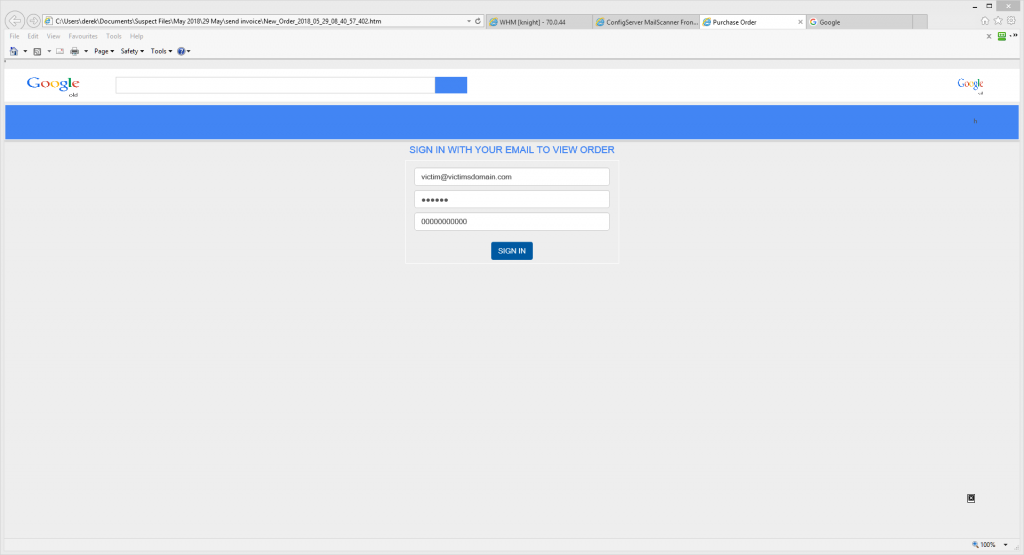
After you fill in details you get sent to a page with an image of an invoice or order hosted on http://portiahairstyles.org/petrurd.php while your stolen details are sent to http://portiahairstyles.org/ppp.php ( which is either a compromised website or has been newly set up to perform this phishing attack) The home page has a default site now set up message from Inmotion Hosting. on Ip 209.182.200.172
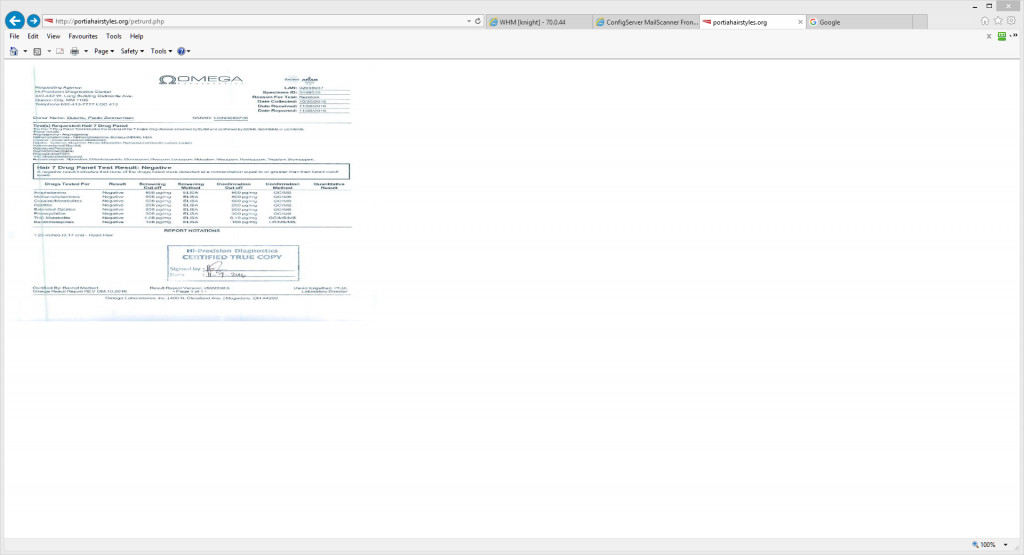
Then you get forwarded to a genuine Gmail page
We all get very blasé about phishing and think we know so much that we will never fall for a phishing attempt. Don’t assume that all attempts are obvious. Watch for any site that invites you to enter ANY personal or financial information. It might be an email that says “you have won a prize” or “sign up to this website for discounts, prizes and special offers”
Please read our How to protect yourselves page for simple, sensible advice on how to avoid being infected by this sort of socially engineered malware.
All of these emails use Social engineering tricks to persuade you to open the attachments that come with the email. Whether it is a message saying “look at this picture of me I took last night” and it appears to come from a friend or is more targeted at somebody who regularly is likely to receive PDF attachments or Word .doc attachments or any other common file that you use every day. Or whether it is a straight forward attempt, like this one, to steal your personal, bank, credit card or email and social networking log in details. Be very careful when unzipping them and make sure you have “show known file extensions enabled“, And then look carefully at the unzipped file. If it says .EXE then it is a problem and should not be run or opened.
Email Headers:
| IP | Hostname | City | Region | Country | Organisation |
|---|---|---|---|---|---|
| 41.74.205.119 | za-smtp-delivery-119.mimecast.co.za | ZA | AS37235 Mimecast South Africa | ||
| 10.33.36.70 | Private IP | ||||
Received: from za-smtp-delivery-119.mimecast.co.za ([41.74.205.119]:20374)
by My Email Server with esmtps (TLSv1.2:ECDHE-RSA-AES256-SHA384:256)
(Exim 4.91)
(envelope-from <[email protected]>)
id 1fNYc0-0003TP-H8
for [email protected]; Tue, 29 May 2018 08:00:05 +0100
Subject: Send invoice for payment
Message-ID: <Mimecast.da8.a66d528986070677.163aab20bc8@za-sl-28.za.mimecast.lan>
From: “Moolman, Enrico” <[email protected]>
Date: Tue, 29 May 2018 08:59:45 +0200
MIME-Version: 1.0
Received: from null (za-sl-28.za.mimecast.lan [10.33.36.70]) (Using TLS) by
za-smtp-1.mimecast.co.za with ESMTP id
za-mta-35-8013f-a119c55e-ac24-4cc9-8712-4769bd42fe5f-1; Tue, 29 May 2018
08:59:47 +0200
X-MC-Unique: 8013f-a119c55e-ac24-4cc9-8712-4769bd42fe5f-1
Content-Type: multipart/mixed;
boundary=”MCBoundary=_11805290859450041″
