We see lots of phishing attempts for Paypal login account credentials. This one is slightly different than many others, mainly in the way the phisher has set up the phishing site. In Internet Explorer you get a “site Hacked” message but in Firefox or Chrome, you get the PayPal Phishing pages. I don’t quite know what the phishers have done wrong to stop this working in Internet Explorer, or what protections Internet Explorer has that other browsers don’t have.
In this case and in a lot of other phishing attempts (https://www.wordfence.com/blog/2017/04/chrome-firefox-unicode-phishing/) Internet Explorer is much safer than Google Chrome or Firefox. We are so used to seeing Security professionals and tech news sites blasting out stop using Internet Explorer it is dangerous. Use Google Chrome or Firefox.
Well this week the boot is on the other foot and they should all be saying stop using Google Chrome and Firefox, they are too dangerous to use. But of course they won’t and will continue to bash Microsoft regardless.
They use email addresses and subjects that will entice a user to read the email and open the attachment. These definitely do not come from a “Trusted Sender” The spelling and grammar mistakes in the email are more than enough to raise red flags. BUT we read what we “think” we are reading and automatically compensate for minor errors like these without thinking about it.
Remember many email clients, especially on a mobile phone or tablet, only show the Name in the From: and not the bit in <domain.com >. That is why these scams and phishes work so well.
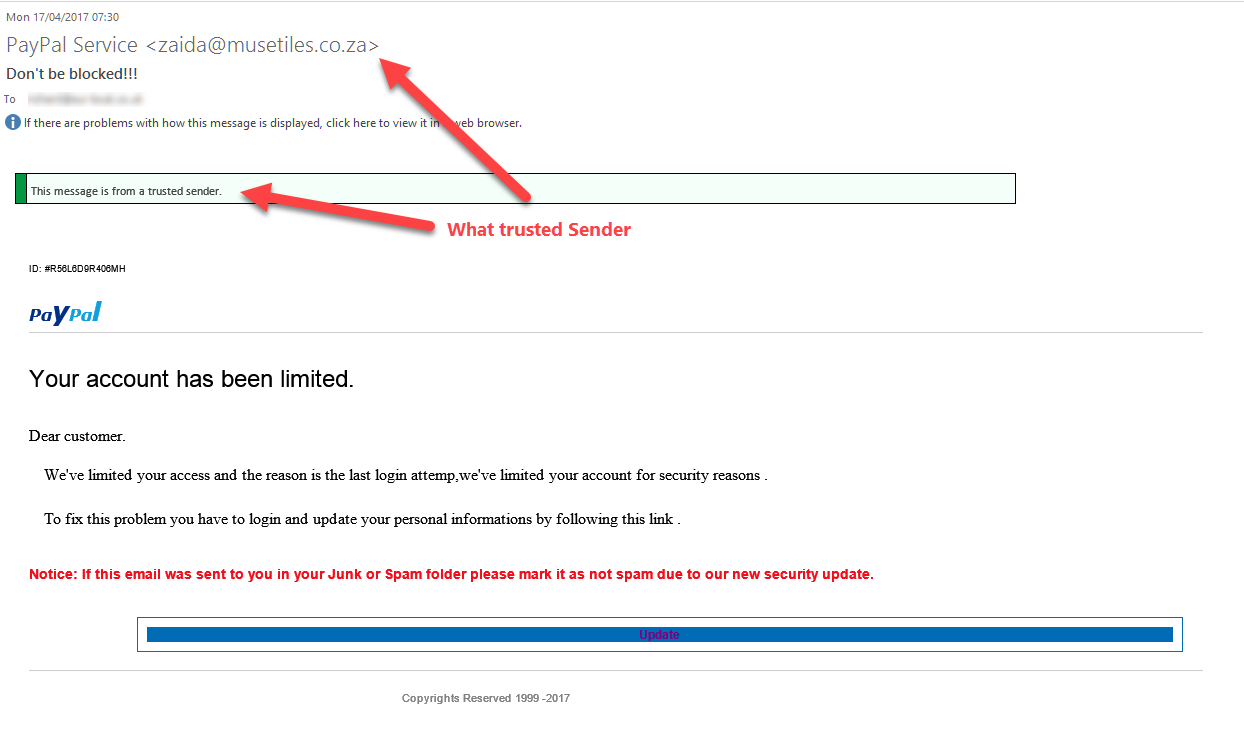
The email looks like:
From: PayPal Service <[email protected]>
Date: Mon 17/04/2021 07:30
Subject: Don’t be blocked!!!
Body Content:
This message is from a trusted sender. ID: #R56L6D9R406MH
ΡαyΡαl
Your account has been limited.
Dear customer.
We’ve limited your access and the reason is the last login attemp,we’ve limited your account for security reasons .
To fix this problem you have to login and update your personal informations by following this link .
Notice: If this email was sent to you in your Junk or Spam folder please mark it as not spam due to our new security update.
Update
Cοpyrights Reserved 1999 -2021
Screenshot:
 Email Headers:
Email Headers:
| IP | Hostname | City | Region | Country | Organisation |
|---|---|---|---|---|---|
| 129.232.250.56 | outgoing2.jnb.host-h.net | ZA | AS37153 HETZNER (Pty) Ltd | ||
| 196.22.132.24 | www24.jnb1.host-h.net | ZA | AS37153 HETZNER (Pty) Ltd | ||
| 77.157.11.191 | 191.11.157.77.rev.sfr.net | Boulogne-Billancourt | �le-de-France | FR | AS15557 Societe Francaise du Radiotelephone S.A. |
Received: from outgoing2.jnb.host-h.net ([129.232.250.56]:60747)
by knight.knighthosting.co.uk with esmtps (TLSv1.2:ECDHE-RSA-AES256-GCM-SHA384:256)
(Exim 4.89)
(envelope-from <[email protected]>)
id 1d00Ao-0007wL-Rw
for richard@[redacted]; Mon, 17 Apr 2021 07:30:07 +0100
Received: from www24.jnb1.host-h.net ([196.22.132.24])
by antispam2-jnb1.host-h.net with esmtpsa (TLSv1.2:AES128-SHA:128)
(Exim 4.86)
(envelope-from <[email protected]>)
id 1d00Am-0002vS-Kq
for richard@[redacted]; Mon, 17 Apr 2021 08:30:05 +0200
Received: from 191.11.157.77.rev.sfr.net ([77.157.11.191] helo=SERVEURICAR)
by www24.jnb1.host-h.net with esmtpa (Exim 4.80)
(envelope-from <[email protected]>)
id 1d00Al-0000Ov-B9
for richard@[redacted]; Mon, 17 Apr 2021 08:30:03 +0200
From: “=?utf-8?Q?PayPal=20Service?=” <[email protected]>
To: “=?utf-8?Q?richard=[redacted]=2Eco=2Euk?=” <richard@[redacted];>
Reply-To: [email protected]
Date: Mon, 17 Apr 2021 09:30:03 +0300
Subject: =?utf-8?Q?Don=27t=20be=20blocked=21=21=21?=
MIME-Version: 1.0
Content-Type: multipart/alternative;
boundary=”_=aspNetEmail=_71359708a1e445838a93feed4cf9e4e7″
Message-ID: <SERVEURICAR9795955f32274d1987edd3ebcdc2d8f2@SERVEURICAR>
X-Authenticated-Sender: [email protected]
X-Virus-Scanned: Clear (ClamAV 0.99.2/23303/Sun Apr 16 22:56:55 2021)
X-Originating-IP: 196.22.132.24
X-SpamExperts-Domain: musetiles.co.za
X-SpamExperts-Username:
Authentication-Results: host-h.net; auth=pass (login) [email protected]
X-SpamExperts-Outgoing-Class: unsure
X-SpamExperts-Outgoing-Evidence: Combined (0.78)
X-Recommended-Action: accept
X-Filter-ID: s0sct1PQhAABKnZB5plbIeLcbzRWUH+yg5LMHYqxYMwibKYD/zmkdhljSpBlvrzs0z6bhalFEM/p
jPCQA+BAlqwVHYW9XhAhD+EDHaoyelZ0rhgVyUSmNw6E4mJY1szEnrIkZp2mn6Qry0vFKTHPqKd3
1FAKOoQhiKfgUnnmsuAJ/a5Vy6LYFnrtfORtxnuxsUuU6VZH37mjWtEw6QruvRZHm64bq5wuus8r
8fMukXh1ya1NxZI4oPlEBJXODbuK9y70qoB6PXKywtJxAOTSX7wqyT5p50x81ZKcmzCu2U0n/UGl
BalePiOM+VHM/3pEwaPVj4uCBOOSfEjCAVrAO4/Ia6YN5m0MsQWfYUYaa1JqFLzIZyFEJXIkx9vV
KSAQRP8RlJxhRWbjCUuEQlBB7OKVse1sVhWabI0/+PN3sIKnctAlhdhhUbxXaXWArqeMVVGlec3B
oP8JeAQwweke7Xgpvl8KUE7flMx5e3A1r/Ci8gnN+VQO0b1vxxohqsS9MYG9IT75mVNYDdt/wZjx
LcXBEEwpWC6eCe+JHwcSeHtzqO3J08MD84K5V0KNXe9KQ6S/gw/C5sL3rCUnYF65Rn20gevXHWUr
3HUdVoLfJ1x6KLvx+FTnVjKwxDT7GgzkZcnB5G4y3tfLxBrP8L+YEvVdyPOcJwZf+mGEJuzRRI8B
1yVUELcQg+T0aA92QEY8TXLbSalD9T0qjTYb6Lai5s8xRqkb8oR7ewerzNWinRT6Gew4jH22624b
XqDj0nE6ZBHCCVMTuRsprxxnVy+CZiIpkk35MI9DVHxM/A6I+CPmiECopDN7iPjz1P/GYDTKnj6h
kgKab1bCwOy1k0tAobWmnVfiwEawIHqtp6BtGwA=
X-Report-Abuse-To: [email protected]
Note: Only the final IP address outside of your network in the Received: fields can be trusted as others can be spoofed
If you follow the link when you use Internet Explorer you start with http://www.asclepiade.ch/sites/default/files/languages/red.html which redirects you to https://indimedia.co.uk/kasfolio/iceage3overlay/english/pp/
you see a webpage looking like this:
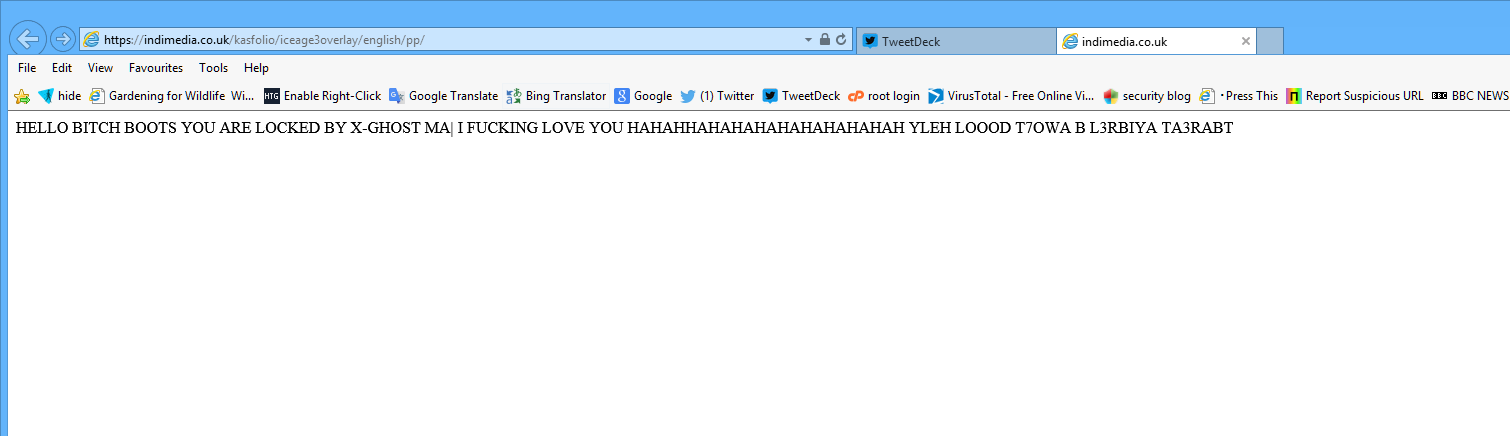
BUT if you use Firefox or Google Chrome, then you get http://www.asclepiade.ch/sites/default/files/languages/red.html which redirects you to https://indimedia.co.uk/kasfolio/iceage3overlay/english/pp/ which redirects to https://indimedia.co.uk/kasfolio/iceage3overlay/english/pp/login?cmd=_signin&dispatch=8b262247e1b6f7c468c785df9&locale=en_GB and gives the typical PayPal phishing page ( you get a different random dispatch= number each time)
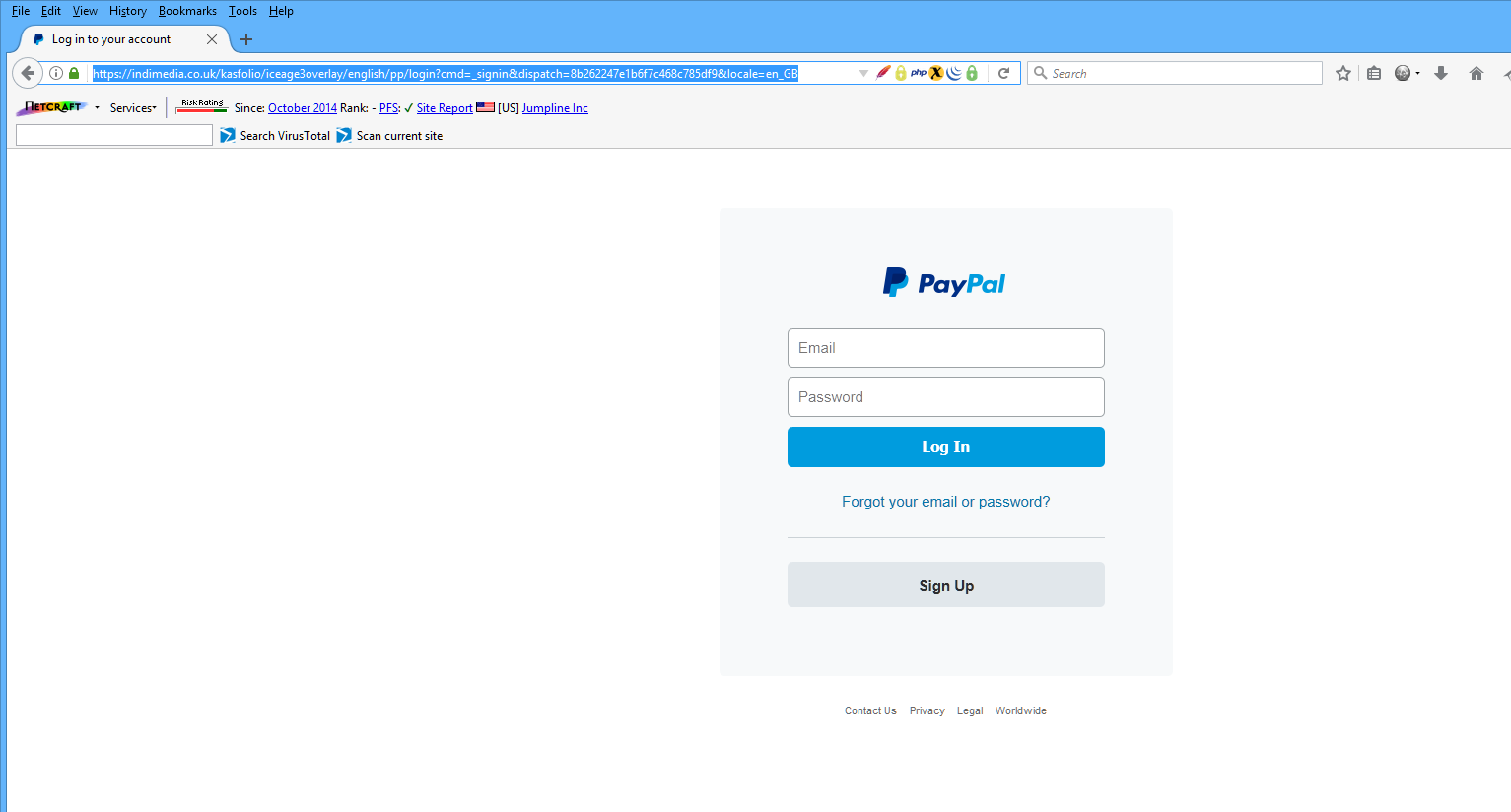
Enter an email address and password and you get
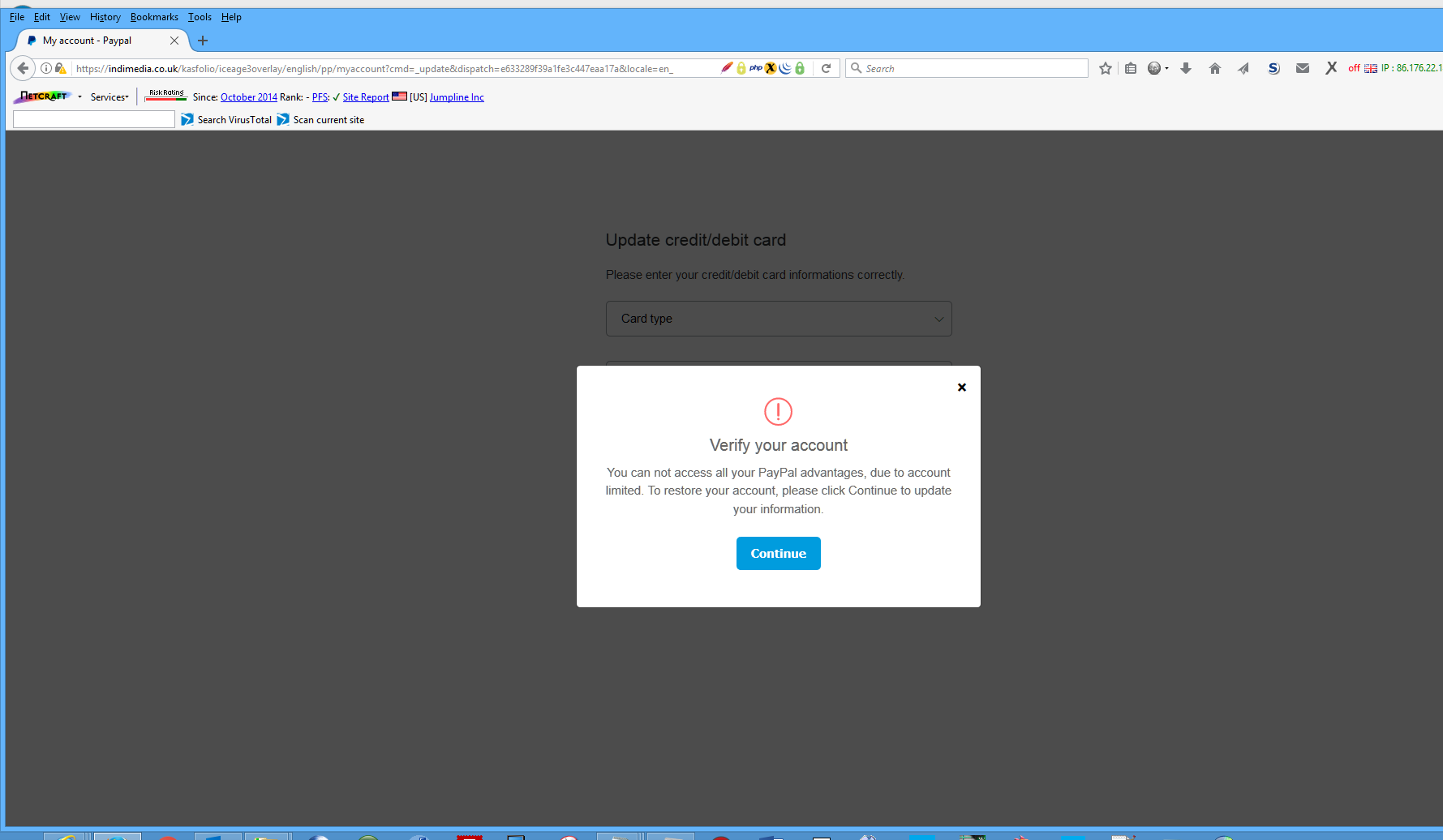
Where pressing continue takes you to the usual give me your credit card, bank account, address, phone number and any other information they can think of, to be able to totally steal your identity and all financial accounts.
We all get very blasé about phishing and think we know so much that we will never fall for a phishing attempt. Don’t assume that all attempts are obvious. Watch for any site that invites you to enter ANY personal or financial information. It might be an email that says “you have won a prize” or “sign up to this website for discounts, prizes and special offers”
Please read our How to protect yourselves page for simple, sensible advice on how to avoid being infected by this sort of socially engineered malware.
All of these emails use Social engineering tricks to persuade you to open the attachments that come with the email. Whether it is a message saying “look at this picture of me I took last night” and it appears to come from a friend or is more targeted at somebody who regularly is likely to receive PDF attachments or Word .doc attachments or any other common file that you use every day. Or whether it is a straight forward attempt, like this one, to steal your personal, bank, credit card or email and social networking log in details.
Be very careful when unzipping them and make sure you have “show known file extensions enabled“, And then look carefully at the unzipped file. If it says .EXE then it is a problem and should not be run or opened.
