Another malware campaign using malformed RTF files involving Microsoft Office Equation Editor exploits to extract or drop a zip file from an embedded ole object containing the payload and an “innocent” lure doc to be displayed. Today it looks like CVE-2017-8570. The payload is Azorult.
This is quite an involved, devious chain of delivery which after opening the word doc ( RTF) attachment to the email it very quickly partially opens & then immediately closes and extracts the contents of a zip containing a Fake Word doc & the malware payload. It then displays the fake word doc in place of the original RTF doc attachment, that in this case is the source code of a phishing HTML page. ( previous versions have been fake invoices or order docs.) and silently runs the payload without you realising anything has happened.
All you think has happened is ” Oh Hell Word has crashed again ” which is not unusual and automatically re-opens itself. You do get a very quick flash of a warning or alert about linked files, but somehow the criminals have managed to bypass the usual Word inbuilt protections & download the files without user interaction. This should have been fixed with an update to all supported versions of Microsoft Office starting In July 2017 and subsequent office updates.
Note: I have only run this malware on an online sandbox, that deliberately has lower security settings, so malware payloads can be easily retrieved. It is very possible that a real computer that is fully updated will not be as vulnerable to this exploit & malware delivery method and will require user interaction, clicking yes or allow to several warning prompts.
However we know that lots of consumers & small businesses and even some larger corporations, charities, Government departments etc. do not routinely update or upgrade Office to recent versions. I still frequently see old, unsupported versions of Office remaining in use. I even see Office XP & 2003 very frequently. All versions prior to Office 2010 are vulnerable to this & many other exploits. The July 2017 Update for Office 2007 should have fixed this one but I wouldn’t 100% guarantee it because Office 2007 stopped getting security updates in October 2017. We have seen continual refinements to the various Equation editor exploits and without your office programs being updated, we cannot guarantee that older updates will fully protect you.
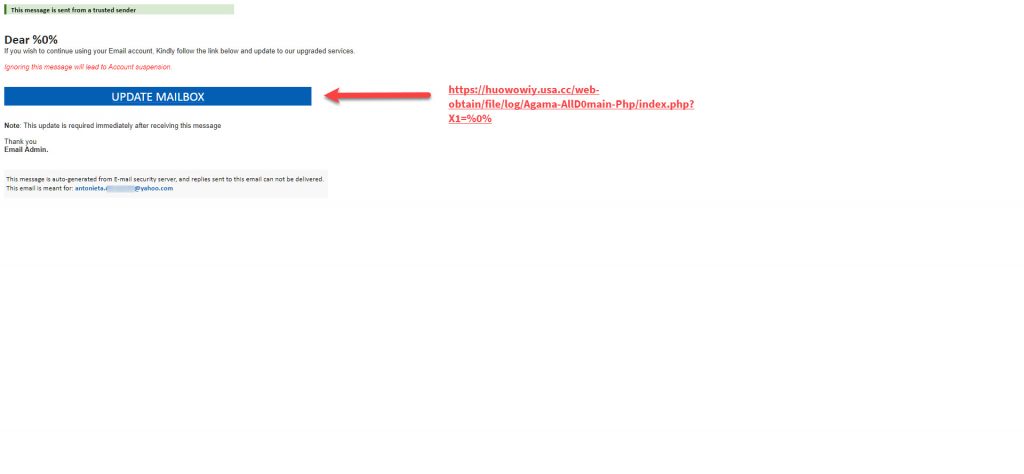
You can see the fake word doc contents in the video on Anyrun. I have converted the html code to display the “phishing page” that I think the criminals intended to be downplayed instead of the code, hoping to also steal your details that way, if the Azorult payload got blocked on the computer. The domain in the link “https://huowowiy.usa.cc/web-obtain/file/log/Agama-AllD0main-Php/index.php?X1=%0%” does not appear to exist, so either hasn’t yet been created or has already been removed by the free domain name providers. A quick look up in Virus Total does show this url was previously used in a phishing scam in Late September 2018. Although this domain was previously removed does not mean it cannot be re-used. We have previously frequently seen free providers & many other domain registrars that remove “bad” domains, but only block the use for a certain amount of time, not permanently. This is why we often see the same “bad” domains popping up in phishing or malware campaigns every few months or years.
They are using email addresses and subjects that will scare or entice a user to read the email and open the attachment. A very high proportion are being targeted at small and medium size businesses, with the hope of getting a better response than they do from consumers.
Remember many email clients, especially on a mobile phone or tablet, only show the Name in the From: and not the bit in <domain.com >. That is why these scams and phishes work so well.
list.doc Current Virus total detections: AnyrunApp |
This malware word doc/ rtf extracts kulebiaka.ZiP (VirusTotal) that displays Gondi.doc ( a harmless lure doc) VirusTotal and the azorult payload saver.scr Virustotal |
C2: “http://blog.tideisun.com.cn/wp-obtain/new/file/js/index.php”
You can now submit suspicious sites, emails and files via our Submissions system
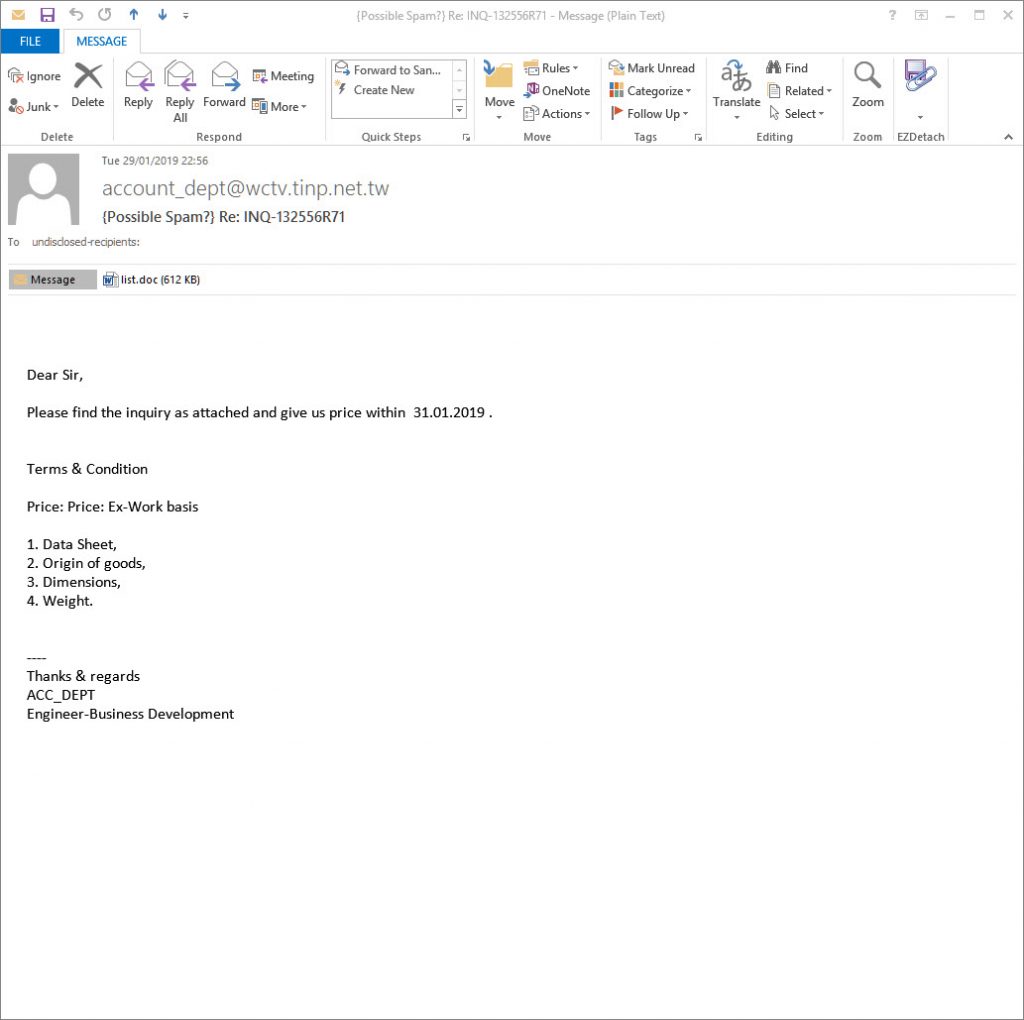
The email looks like:
From: [email protected]
Date: Tue 29/01/2019 22:56
Subject: Re: INQ-132556R71
Attachment: list.doc
Body content:
Dear Sir,
Please find the inquiry as attached and give us price within 31.01.2019 .
Terms & Condition
Price: Price: Ex-Work basis
Data Sheet,
Origin of goods,
Dimensions,
Weight.
—-
Thanks & regards
ACC_DEPT
Engineer-Business Development
Screenshot:
All the alleged senders, companies, names of employees, phone numbers, amounts, reference numbers etc. mentioned in the emails are all innocent and are just picked at random. Some of these companies will exist and some won’t. Don’t try to respond by phone or email, all you will do is end up with an innocent person or company who have had their details spoofed and picked at random from a long list that the bad guys have previously found . The bad guys choose companies, Government departments and other organisations with subjects that are designed to entice you or alarm you into blindly opening the attachment or clicking the link in the email to see what is happening.
This email attachment contains what appears to be a genuine word doc or Excel XLS spreadsheet with either a macro script or an embedded OLE object that when run will infect you.
Modern versions of Microsoft office, that is Office 2010, 2013, 2016 and Office 365 should be automatically set to higher security to protect you.
By default protected view is enabled and macros are disabled, UNLESS you or your company have enabled them. If protected view mode is turned off and macros are enabled then opening this malicious word document will infect you, and simply previewing it in windows explorer or your email client might well be enough to infect you. Definitely DO NOT follow the advice they give to enable macros or enable editing to see the content.
Most of these malicious word documents either appear to be totally blank or look something like these images when opened in protected view mode, which should be the default in Office 2010, 2013, 2016 and 365. Some versions pretend to have a digital RSA key and say you need to enable editing and Macros to see the content. Do NOT enable Macros or editing under any circumstances.
What Can Be Infected By This
At this time, these malicious macros only infect windows computers. They do not affect a Mac, IPhone, IPad, Blackberry, Windows phone or Android phone. The malicious word or excel file can open on any device with an office program installed, and potentially the macro will run on Windows or Mac or any other device with Microsoft Office installed. BUT the downloaded malware that the macro tries to download is windows specific, so will not harm, install or infect any other computer except a windows computer. You will not be infected if you do not have macros enabled in Excel or Word. These Macros do not run in “Office Online” Open Office, Libre Office, Word Perfect or any other office program that can read Word or Excel files.
Please read our How to protect yourselves page for simple, sensible advice on how to avoid being infected by this sort of socially engineered malware. Also please read our post about word macro malware and how to avoid being infected by them
Be very careful with email attachments. All of these emails use Social engineering tricks to persuade you to open the attachments that come with the email. It might be a simple message saying “look at this picture of me I took last night” that appears to come from a friend. It might be a scare ware message that will make you open the attachment to see what you are accused of doing. Frequently it is more targeted at somebody ( small companies etc.) who regularly receive PDF attachments or Word .doc attachments or any other common file that you use every day, for example an invoice addressed to [email protected].
The basic rule is NEVER open any attachment to an email, unless you are expecting it. Now that is very easy to say but quite hard to put into practice, because we all get emails with files attached to them. Our friends and family love to send us pictures of them doing silly things, or even cute pictures of the children or pets. Many of us routinely get Word, Excel or PowerPoint attachments in the course of work or from companies that we already have a relationship with.
Never just blindly click on the file in your email program. Always save the file to your downloads folder, so you can check it first. A lot of malicious files that are attached to emails will have a faked extension. That is the 3 letters at the end of the file name. Unfortunately windows by default hides the file extensions so you need to Set your folder options to “show known file types. Then when you unzip the zip file that is supposed to contain the pictures of “Sally’s dog catching a ball”, an invoice or receipt from some company for a product or service or receive a Word doc or Excel file report that work has supposedly sent you to finish working on at the weekend, you can easily see if it is a picture or document & not a malicious program. If you see JS or .EXE or .COM or .PIF or .SCR or .HTA .vbs, .wsf , .jse .jar at the end of the file name DO NOT click on it or try to open it, it will infect you.
With these malformed infected word, excel and other office documents that normally contain a vba macro virus, the vital thing is do not open any office document direct from your email client or the web. Always save the document to a safe location on your computer, normally your downloads folder or your documents folder and scan it with your antivirus. Many Antiviruses do not natively detect vba macro-viruses in real time protection and you need to enable document or office protection in the settings. Do not rely on your Anti-Virus to immediately detect the malware or malicious content. DO NOT enable editing mode or enable macros
All modern versions of word and other office programs, that is 2010, 2013, 2016 and 365, should open all Microsoft office documents that is word docs, excel files and PowerPoint etc that are downloaded from the web or received in an email automatically in “protected view” that stops any embedded malware or macros from being displayed and running. Make sure protected view is set in all office programs to protect you and your company from these sorts of attacks and do not over ride it to edit the document until you are 100% sure that it is a safe document. If the protected mode bar appears when opening the document DO NOT enable editing mode or enable macros the document will look blank or have a warning message, but will be safe.
Be aware that there are a lot of dodgy word docs spreading that WILL infect you with no action from you if you are still using an out dated or vulnerable version of word. This is a good reason to update your office programs to a recent version and stop using office 2003 and 2007. Many of us have continued to use older versions of word and other office programs, because they are convenient, have the functions and settings we are used to and have never seen a need to update to the latest super-duper version. The risks in using older version are now seriously starting to outweigh the convenience, benefits and cost of keeping an old version going.
I strongly urge you to update your office software to the latest version and stop putting yourself at risk, using old out of date software.
IOC:
https://huowowiy.usa.cc/web-obtain/file/log/Agama-AllD0main-Php/index.php?X1=%0%
Main object- “list.doc”
sha256 c757740e9295565b363f0e4464514971047648c3309df1fa7cd455cfd34ad8f6
sha1 4e14c9566594feabe8212e8ab6955ac65607bc32
md5 62f446398209fa233340a628e65d5ed6
Displayed Lure
Gondi.doc
80ae0226822b684927280c63ca9f4e683c121fa62715e02909decc298c03b506
6291d5a22fce652360616bd330e07082
46901354d7929e8e5e7c777640ab5a3f42784406
Dropped executable file
C:\Users\admin\AppData\Local\Temp\saver.scr
00b457972708151f1cf613af2083e82f3b962df4c11420e4515e00226376337e
df1e53edcc09554e3fe1a372ae21742b27f1d16c
9677e2c641f4e84bb70daa4151072d2b
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-crt-filesystem-l1-1-0.dll 7633774effe7c0add6752ffe90104d633fc8262c87871d096c2fc07c20018ed2
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-profile-l1-1-0.dll 8eb5270fa99069709c846db38be743a1a80a42aa1a88776131f79e1d07cc411c
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-crt-multibyte-l1-1-0.dll 66abf3a1147751c95689f5bc6a259e55281ec3d06d3332dd0ba464effa716735
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-heap-l1-1-0.dll 44f6df4280c8ecc9c6e609b1a4bfee041332d337d84679cfe0d6678ce8f2998a
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-crt-locale-l1-1-0.dll 565a2eec5449eeeed68b430f2e9b92507f979174f9c9a71d0c36d58b96051c33
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-timezone-l1-1-0.dll 24c9aa0b70e557a49dac159c825a013a71a190df5e7a837bfa047a06bba59eca
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-crt-math-l1-1-0.dll bece7bab83a5d0ec5c35f0841cbbf413e01ac878550fbdb34816ed55185dcfed
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-rtlsupport-l1-1-0.dll 2257fea1e71f7058439b3727ed68ef048bd91dcacd64762eb5c64a9d49df0b57
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-crt-private-l1-1-0.dll 65ded8d2ce159b2f5569f55b2caf0e2c90f3694bd88c89de790a15a49d8386b9
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-crt-process-l1-1-0.dll c03124ba691b187917ba79078c66e12cbf5387a3741203070ba23980aa471e8b
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-sysinfo-l1-1-0.dll 4b704b36e1672ae02e697efd1bf46f11b42d776550ba34a90cd189f6c5c61f92
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-crt-runtime-l1-1-0.dll c9bbc07a033bab6a828ecc30648b501121586f6f53346b1cd0649d7b648ea60b
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-crt-heap-l1-1-0.dll f5cf623ba14b017af4aec6c15eee446c647ab6d2a5dee9d6975adc69994a113d
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-synch-l1-2-0.dll 30d99ce1d732f6c9cf82671e1d9088aa94e720382066b79175e2d16778a3dad1
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-crt-environment-l1-1-0.dll c0d75d1887c32a1b1006b3cffc29df84a0d73c435cdcb404b6964be176a61382
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-synch-l1-1-0.dll 5dd4ccd63e6ed07ca3987ab5634ca4207d69c47c2544dfefc41935617652820f
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-processthreads-l1-1-0.dll 9dab884071b1f7d7a167f9bec94ba2bee875e3365603fa29b31de286c6a97a1d
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-util-l1-1-0.dll f7d450a0f59151bcefb98d20fcae35f76029df57138002db5651d1b6a33adc86
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-crt-convert-l1-1-0.dll 3cc1377d495260c380e8d225e5ee889cbb2ed22e79862d4278cfa898e58e44d1
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-crt-conio-l1-1-0.dll 9ca21763c528584bdb4efebe914faaf792c9d7360677c87e93bd7ba7bb4367f2
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-file-l1-2-0.dll c8c499b012d0d63b7afc8b4ca42d6d996b2fcf2e8b5f94cacfbec9e6f33e8a03
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-handle-l1-1-0.dll 945cc64ee04b1964c1f9fcdc3124dd83973d332f5cfb696cdf128ca5c4cbd0e5
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-debug-l1-1-0.dll c310cc91464c9431ab0902a561af947fa5c973925ff70482d3de017ed3f73b7d
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-file-l2-1-0.dll c85dc081b1964b77d289aac43cc64746e7b141d036f248a731601eb98f827719
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-string-l1-1-0.dll 7670fdede524a485c13b11a7c878015e9b0d441b7d8eb15ca675ad6b9c9a7311
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-errorhandling-l1-1-0.dll a97dcca76cdb12e985dff71040815f28508c655ab2b073512e386dd63f4da325
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-file-l1-1-0.dll 7ea06b7050f9ea2bcc12af34374bdf1173646d4e5ebf66ad690b37f4df5f3d4e
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-memory-l1-1-0.dll bb33a9e906a5863043753c44f6f8165afe4d5edb7e55efa4c7e6e1ed90778eca
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-datetime-l1-1-0.dll 90fae0e7c3644a6754833c42b0ac39b6f23859f9a7cf4b6c8624820f59b9dad3
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-libraryloader-l1-1-0.dll bb25ccf8694d1fcfce85a7159dcf6985fdb54728d29b021cb3d14242f65909ce
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-namedpipe-l1-1-0.dll c4f60f911068ab6d7f578d449ba7b5b9969f08fc683fd0ce8e2705bbf061f507
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-interlocked-l1-1-0.dll deccd75fc3fc2bb31338b6fe26deffbd7914c6cd6a907e76fd4931b7d141718c
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-processthreads-l1-1-1.dll 91eeb842973495deb98cef0377240d2f9c3d370ac4cf513fd215857e9f265a6a
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-processenvironment-l1-1-0.dll 96898930ffb338da45497be019ae1adcd63c5851141169d3023e53ce4c7a483e
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-localization-l1-2-0.dll 03ad57c24ff2cf895b5f533f0ecbd10266fd8634c6b9053cc9cb33b814ad5d97
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-console-l1-1-0.dll 94a5df1227818edbfd0d5091c6a48f86b4117c38550343f780c604eee1cd6231
sha256 C:\Users\admin\AppData\Local\Temp\2fda\msvcp140.dll 334e69ac9367f708ce601a6f490ff227d6c20636da5222f148b25831d22e13d4
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-crt-stdio-l1-1-0.dll b1e702b840aebe2e9244cd41512d158a43e6e9516cd2015a84eb962fa3ff0df7
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-crt-utility-l1-1-0.dll a1d1d6b0cb0a8421d7c0d1297c4c389c95514493cd0a386b49dc517ac1b9a2b0
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-crt-string-l1-1-0.dll 73cc56f20268bfb329ccd891822e2e70dd70fe21fc7101deb3fa30c34a08450c
sha256 C:\Users\admin\AppData\Local\Temp\2fda\freebl3.dll 393ae7f06fe6cd19ea6d57a93dd0acd839ee39ba386cf1ca774c4c59a3bfebd8
sha256 C:\Users\admin\AppData\Local\Temp\2fda\mozglue.dll 830533bb569594ec2f7c07896b90225006b90a9af108f49d6fb6bebd02428b2d
sha256 C:\Users\admin\AppData\Local\Temp\2fda\nss3.dll f0e6210d4a0d48c7908d8d1c270449c91eb4523e312a61256833bfeaf699abfb
sha256 C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-crt-time-l1-1-0.dll 69885fd581641b4a680846f93c2dd21e5dd8e3ba37409783bc5b3160a919cb5d
sha256 C:\Users\admin\AppData\Local\Temp\2fda\vcruntime140.dll c40bb03199a2054dabfc7a8e01d6098e91de7193619effbd0f142a7bf031c14d
sha256 C:\Users\admin\AppData\Local\Temp\2fda\nssdbm3.dll 541a293c450e609810279f121a5e9dfa4e924d52e8b0c6c543512b5026efe7ec
sha256 C:\Users\admin\AppData\Local\Temp\2fda\softokn3.dll 9a7f11c212d61856dfc494de111911b7a6d9d5e9795b0b70bbbc998896f068ae
sha256 C:\Users\admin\AppData\Local\Temp\2fda\ucrtbase.dll 0bb8c77de80acf9c43de59a8fd75e611cc3eb8200c69f11e94389e8af2ceb7a9
DNS requests
domain blog.tideisun.com.cn
Connections
ip 45.192.167.126
HTTP/HTTPS requests
url http://blog.tideisun.com.cn/wp-obtain/new/file/js/index.php
