Following on from THIS post earlier today which has created some discussion on Twitter amongst various InfoSec professionals, I want to expand slightly.
Whether this is actually an APT ( Advanced Persistent Threat) or not is open to discussion. I would say Yes!. Although this and other similar Remote Access Trojans are commonly used and normally eventually discovered by an IT person or antivirus, hundreds, thousands or even millions of attacks go unnoticed. In this case, there are enough warning clues in the email to alert a user to a problem: Bad spelling, dodgy grammar, invalid addresses and phone numbers etc.
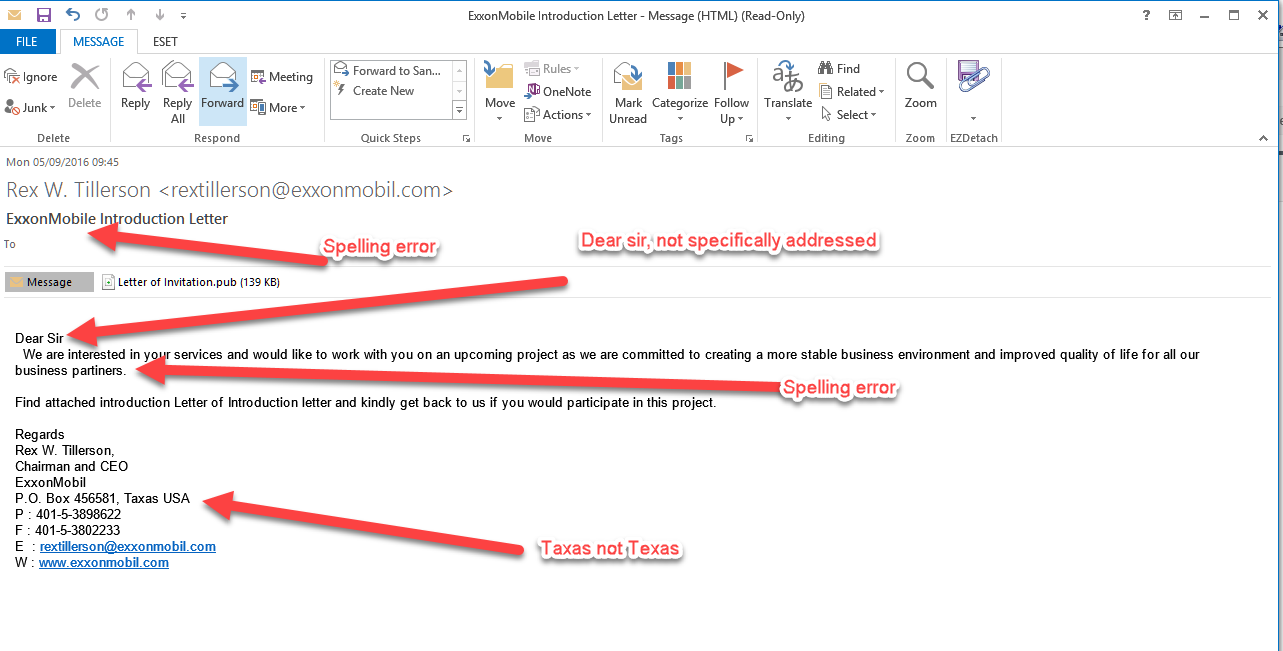
An alert end user could just delete the email without informing IT or running the attached file. If only 1 or 2 copies were sent to each company and 1 was deleted but another one run, we never see the scale or potential of the attack. We normally only hear about large scale attacks like Dridex, Locky, Crypto-locker, Cerber, Java Adwind and other widespread scattershot attacks.
Individual or small scale ones stay under the radar and targeted /infiltrated companies frequently keep it all totally quiet to avoid shareholder losses and market instabilities. If a user never sees anything happening on their computer they won’t know they have been infiltrated and these APT / R A T are designed to stay stealthy and quiet with minimal and indeed no outward signs whatsoever.
The computer behaves normally, so the user has no reason to believe they did anything wrong in opening the email & running the file. They get similar files every day form colleagues, so why was this one any different.
The actual delivered malware turned out to be a reasonably common RAT ( Remote Access Trojan) However not well detected by security / Antivirus companies because of the crypted nature of the beast. A crypted malware or indeed any file is one where the developer/author /writer uses anIs it an APT encryption algorithm to change its appearance and behaviour so that a scanning program ( antivirus) cannot detect the file as malicious. Symantec explains what a cryptor does “its purpose is to obfuscate a malicious executable file’s contents so that it can still run as it was intended, but remain unrecognizable to antivirus software.”
This is not the same as an Encrypted file where normally somebody is preventing access to the file completely by anybody and anything. This is either done as a security measure by tools like Bitlocker or Truecrypt amongst others which stop unauthorised people seeing the contents of the file. Or by a malicious person who locks the files until you pay a ransom to get access back.
My view is, if we can block the delivery mechanism, it really doesn’t matter what the end result malware is. If it cannot get to the computer, the “victim” is safe. Usual macro delivery method is word or excel where the bad guys get the most bang for their bucks.
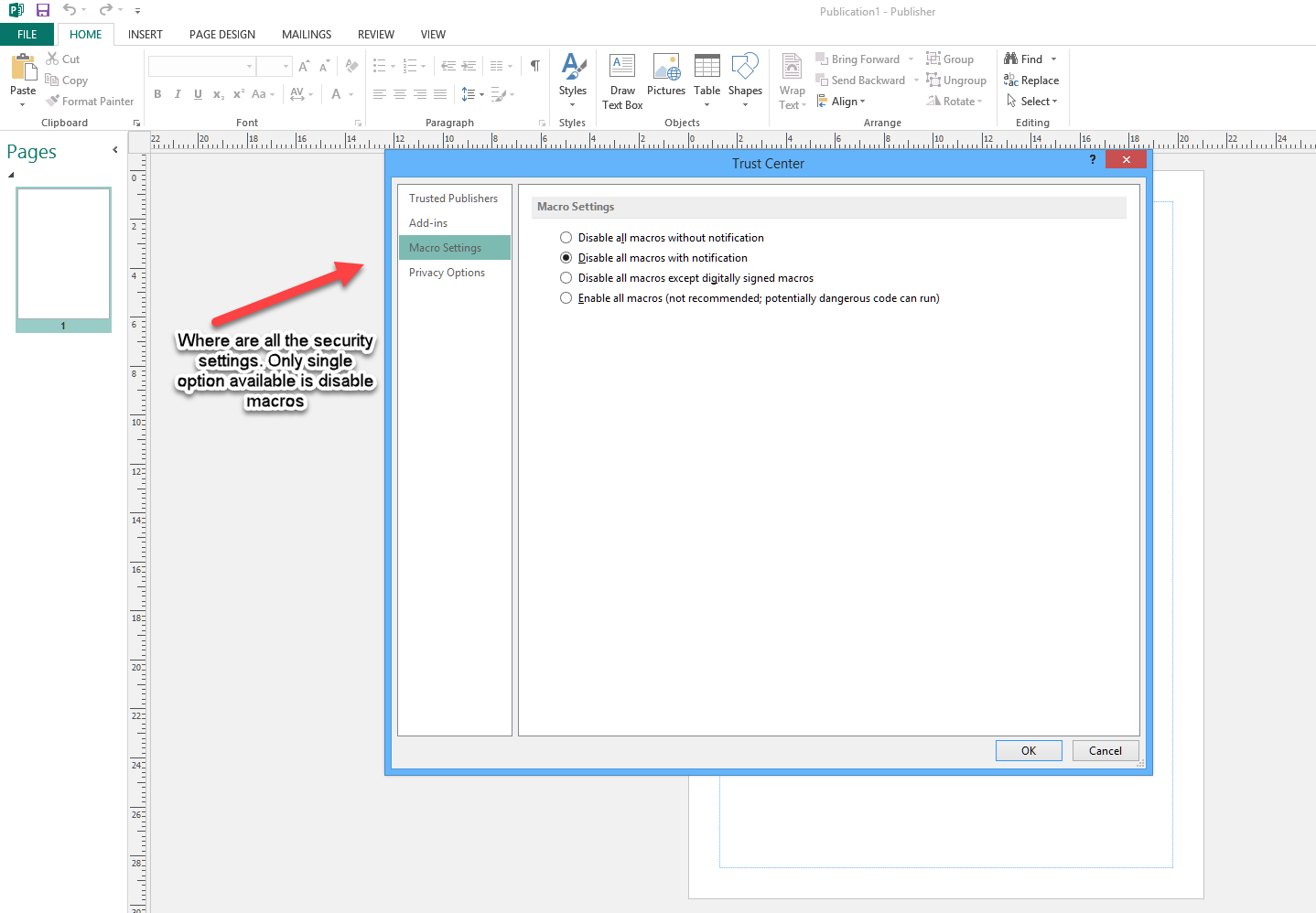
What has concerned me the most today is the “new” approach from these criminals in using Microsoft Publisher with embedded macros to distribute the dropper. For some unknown and unfathomable reason Microsoft have not just dropped the ball with security in Microsoft Publisher but allowed the ball to be so far completely kicked out of play that it is almost like the program comes from the last century with minimal if any security.
Over the last couple of years Microsoft have done quite a good job of tightening security in most office programs, especially Word and Excel where Macros and embedded ole objects are now very difficult to run from the internet, web or via email. Macros are disabled by default and in Word & Excel, you can easily prevent users from enabling them. Also Word, Excel and PowerPoint all have Protected view / Active X protections / Trusted locations / warning bar see technet
For some reason which totally escapes me, Microsoft have not enabled any of these in Publisher, except macros protection and that is so easy for a user to over ride. If you compare the available settings in these 2 screenshots, you see what I mean.