This example is an email containing the subject of “Advice of Service Charge” saying that you have a service charge to pay of £42,243.52 is really going to give a few recipients quite a shock. This pretends to come from RBS, Royal Bank of Scotland but actually coming from “[email protected]” which is a look-a-like, typo-squatted or other domain that can easily be misidentified, mistaken or confused with the genuine site, with a malicious word doc attachment is today’s latest spoof of a well-known company, bank or public authority delivering Trickbot banking Trojan.
However today it looks like the delivery system went wrong and none of the downloaded files actually ran in any online sandbox or VM.
Update finally got a working binary
You can now submit suspicious sites, emails and files via our Submissions system
Email Details
From: Royal Bank of Scotland <[email protected]>
Date: Mon 03/09/2021 12:37
Subject: Advice of Service Charge
Attachment: 03062021_03092021Charge.doc
Body Content:
Advice of Service Charge for the period 3 June 2021 to 3 Sep 2021
The Service Charge accrued on your account is £42,243.52.
This amount will be deducted from your account on July 21 2021.
Basis of Charge
The charge is calculated as a pro rata fee (at £14.081.17 per month)
Service Charge to be applied: -£42,243.52
We have identified a bank systems error, which has regrettably altered the quarterly service charge you currently pay. You might have recently received a Service Charge Advice indicating a substantially higher quarterly fee and we would like to offer our sincere apologies if this is the case.
This problem has been rectified and the amount indicated on the advice will not be debited to your bank account. I would like to stress that the problem is in no way your fault and is purely due to a technical problem within The Royal Bank of Scotland plc.
WE HAVE TAKEN THE OPPORTUNITY TO REVIEW SERVICE CHARGES LEVIED ON YOUR ACCOUNT AND ARE PLEASED TO ADVISE YOU THAT WE WILL, WITH THE EFFECT FROM 1ST OCT 2018, BE MARKING YOUR ACCOUNT EXEMPT OF SERVICE CHARGES IN THE FUTURE. FOR MORE DETAILS PLEASE CHECK ATTACHED DOCUMENT.
Once again please accept my apologies for any inconvenience caused by this technical problem.
Sincerely,
Evangeline Mirk
Level II Senior Officer
Commercial Banking, Royal Bank of Scotland plc
CONFIDENTIALITY NOTICE:The contents of this email message and any attachments are intended solely for the addressee(s)and may contain confidential and/or privileged information and may be legally protected from disclosure. If you are not the recipient of this message or their agent, or if this message has been addressed to you in error, please immediately alert the sender by reply email and then delete this message and any attachments. If you are not the recipient, you are hereby notified that any use, dissemination, copying, or storage of this message or its attachments is strictly prohibited.
Screenshot:
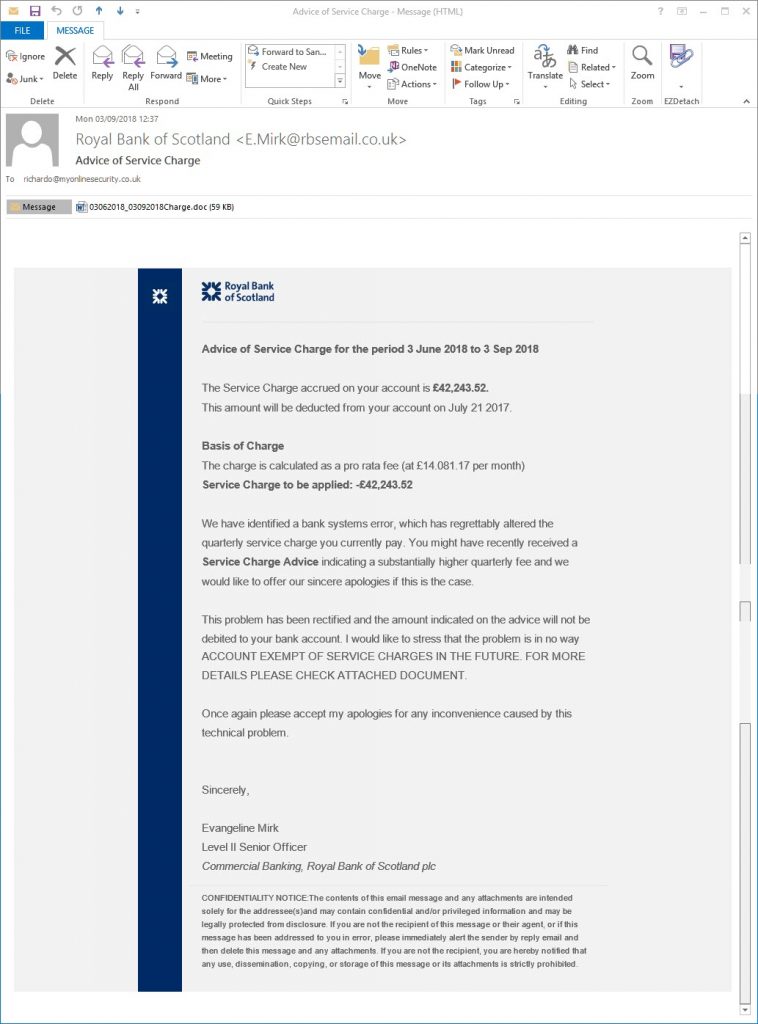 Fake Royal Bank of Scotland email
Fake Royal Bank of Scotland email
RBS has not been hacked or had their email or other servers compromised. They are not sending the emails to you. They are just innocent victims in exactly the same way as every recipient of these emails.
What has happened is that the criminals sending these have registered various domains that look like genuine Company, Bank, Government or message sending services. Normally there is only newly registered domain that imitate Companies House, HMRC, another Government department, a Bank, file hosting service or a message sending service that can easily be confused with the genuine organisation in some way, that are hosted on & sending emails from 4 different servers.. Some days however we do see dozens or even hundreds of fake domains.
Today’s example of the spoofed domain is, as usual, registered via Godaddy as registrar. Because of new GDPR rules we cannot easily find the registrants name or any further details.
rbsemail.co.uk hosted on & sending emails via 66.85.159.40| 185.225.114.57 |37.48.117.19| 94.228.219.214|
Malware Details
03062018_03092018Charge.doc Current Virus total detections | Hybrid Analysis | Anyrun |
This malware doc file downloads from http://atlantisprojects.ca/stard.ust which is a renamed .exe file VirusTotal | Anyrun |Cape Sandbox| Hybrid Analysis |
The alternate Download location is
A 3rd location which was redirected from the second one is which is a renamed .exe file VirusTotal | Anyrun | Anyrun 2 | Gtag Ser0903
Folder for files & config is :
I can’t get the payload to run in Anyrun or Hybrid analysis. I don’t know if it is a damaged file or whether there is some sort of VM / Sandbox protection. Anyrun couldn’t seem to download the files form any location. HA got the files but shows nothing much when run. Cape also crashed so it looks like a damaged payload today.
Update the download direct from gave me a different sha-1 hash and is working
All modern versions of word and other office programs, that is 2010, 2013, 2016 and 365, should open all Microsoft office documents that is Word docs, Excel spreadsheet files and PowerPoint etc that are downloaded from the web or received in an email automatically in “protected view” that stops any embedded malware, macros and DDE “exploit /Feature” and embedded ole objects from being displayed and running.
Make sure protected view is set in all office programs to protect you and your company from these sorts of attacks and do not over ride it to edit the document. If the protected mode bar appears when opening the document DO NOT follow the advice they give to enable macros or enable editing to see the content. The document will have a warning message, but you will be safe.
Be aware that there are a lot of other dodgy word docs spreading that WILL infect you with no action from you, if you are still using an out dated or vulnerable version of word. This is a good reason to update your office programs to a recent version and stop using office 2003 and 2007.
Many of us have continued to use older versions of word and other office programs, because they are convenient, have the functions and settings we are used to and have never seen a need to update to the latest super-duper version.
The risks in using older version are now seriously outweighing the convenience, benefits and cost of keeping an old version going.
What Can Be Infected By This
At this time, these malicious macros only infect windows computers. They do not affect a Mac, IPhone, IPad, Blackberry, Windows phone or Android phone.
The malicious word or excel file can open on any device with an office program installed, and potentially the macro will run on Windows or Mac or any other device with Microsoft Office installed. BUT the downloaded malware that the macro tries to download is windows specific, so will not harm, install or infect any other computer except a windows computer.
You will not be infected if you do not have macros enabled in Excel or Word. These Macros, embedded Oles or DDE do not run in “Office Online” Open Office, Libre Office, Word Perfect or any other office program that can read Word or Excel files.
Please read our How to protect yourselves page for simple, sensible advice on how to avoid being infected by this sort of socially engineered malware. Also please read our post about word macro malware and how to avoid being infected by them
I strongly urge you to update your office software to the latest version and stop putting yourself at risk, using old out of date software.
IOC:
03062018_03092018Charge.doc
MD5: 11e2006d133cfb1777d1cef4d8d77115
SHA-1: 153e0ed7294b9262a6d0070e7d846118e1e0fc99
Download URLs
http://atlantisprojects.ca/stard.ust
http://mustardcafeonline.com/stard.ust
MD5: da7649856879ac5ad29cc8a6d4f40750
SHA1: 530f1b14f4413a521e9128b278e341694397aa5e
http://mustardcafeandgrill.com/stard.ust
MD5: 2ec4eb40c1d05ed0d9d011e2746cdca1
SHA-1: 9ed7ae2084e86446fbacf443421e612fab919cae
Email from: [email protected]
66.85.159.40
185.225.114.57
37.48.117.19
94.228.219.214
